Digital Is Not Enough; Nor Is Paperless
Don't think about just using insurance technology to connect to your customers. Think about connecting your risk management team.

Don't think about just using insurance technology to connect to your customers. Think about connecting your risk management team.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Chris Cheatham is the CEO of <a href="http://riskgenius.com/">Riskgenius</a>, a collaborative contract review application for the insurance industry. Cheatham previously worked as an insurance attorney in Washington, D.C. before deciding to solve the messy document problems he was encountering.
Insurers must follow the lead of airlines and retailers and use quote data to fine-tune prices and features based on each customer's situation.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

John Johansen is a senior vice president at Majesco. He leads the company's data strategy and business intelligence consulting practice areas. Johansen consults to the insurance industry on the effective use of advanced analytics, data warehousing, business intelligence and strategic application architectures.
When insurers get things right and captivate customers, they see a 34% increase in customer retention and a 37% rise in satisfaction.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Bhuvan Thakur is a vice president within the Enterprise Cloud Services business for Capgemini in North America, UK and Asia-Pacific. Thakur has more than 18 years of consulting experience, primarily in the customer relationship management (CRM) and customer experience domain.

Jeff To is the insurance leader for Salesforce. He has led strategic innovation projects in insurance as part of Salesforce's Ignite program. Before that, To was a Lean Six Sigma black belt leading process transformation and software projects for IBM and PwC's financial services vertical.
Market cycles are diminishing greatly because sophisticated analytics let insurers price risks individually, not based on market psychology.

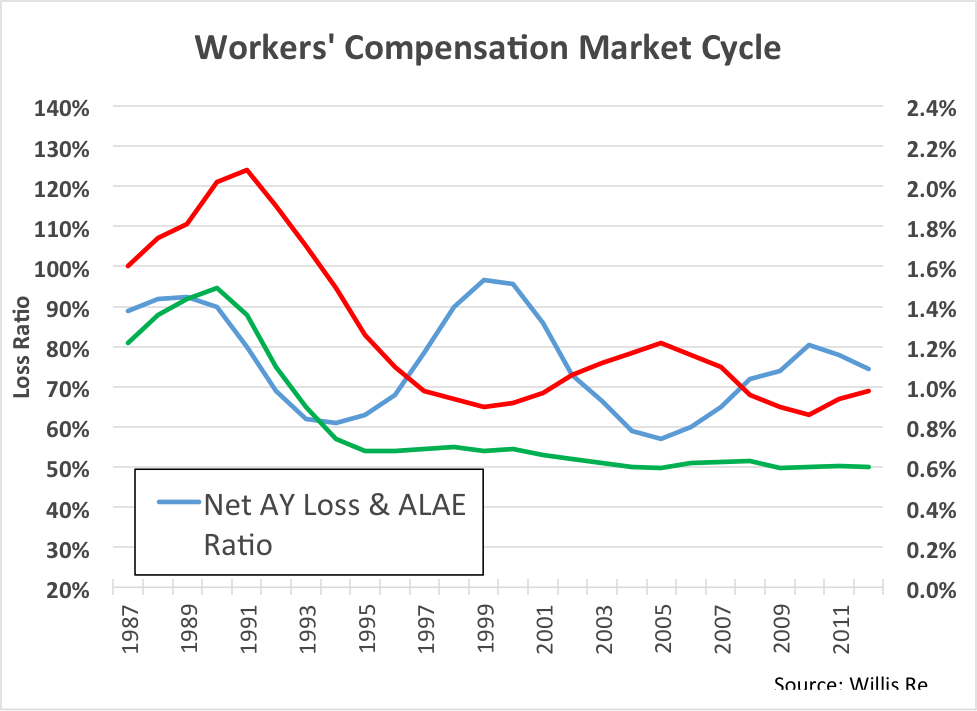 This is an aggregate view of the work comp industry results. The blue line is accident year loss ratio, 1987 to present. See the volatility? Loss ratio is bouncing up and down between 60% and 100%.
Now look at the red line. This is the price line. We see volatility in price, as well, and this makes sense. But what’s the driver here? Is price reacting to loss ratio, or are movements in loss ratio a result of changes in price?
To find the answer, look at the green line. This is the historic loss rate per dollar of payroll. Surprisingly, this line is totally flat from 1995 to the present. In other words, on an aggregate basis, there has been no fundamental change in loss rate for the past 20 years. All of the cycles in the market are the result of just one thing: price movement.
Unfortunately, it appears we have done this to ourselves.
This is an aggregate view of the work comp industry results. The blue line is accident year loss ratio, 1987 to present. See the volatility? Loss ratio is bouncing up and down between 60% and 100%.
Now look at the red line. This is the price line. We see volatility in price, as well, and this makes sense. But what’s the driver here? Is price reacting to loss ratio, or are movements in loss ratio a result of changes in price?
To find the answer, look at the green line. This is the historic loss rate per dollar of payroll. Surprisingly, this line is totally flat from 1995 to the present. In other words, on an aggregate basis, there has been no fundamental change in loss rate for the past 20 years. All of the cycles in the market are the result of just one thing: price movement.
Unfortunately, it appears we have done this to ourselves.
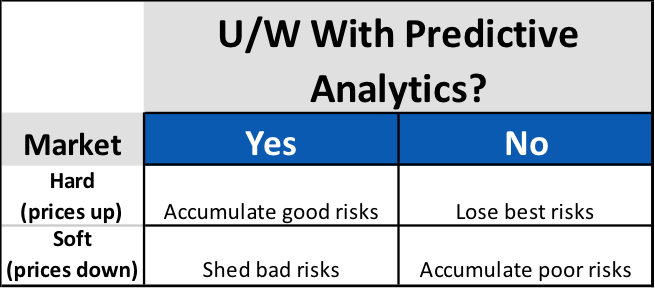 Surprisingly, for carriers using predictive analytics, market cycles present an opportunity to increase profitability, regardless of cycle direction. For the unfortunate carriers not using predictive analytics, the onset of each new cycle phase presents a new threat to portfolio profitability.
Simply accepting that profitability will wax and wane with market cycles isn’t keeping up with the times. Though the length and intensity may change, markets will continue to cycle. Sophisticated carriers know that these cycles present not a threat to profits, but new opportunities for differentiation. Modern approaches to policy acquisition and retention are much more focused on individual risk pricing and selection that incorporate data analytics. The good news is that these data-driven carriers are much more in control of their own destiny, and less subject to market fluctuations as a result.
Surprisingly, for carriers using predictive analytics, market cycles present an opportunity to increase profitability, regardless of cycle direction. For the unfortunate carriers not using predictive analytics, the onset of each new cycle phase presents a new threat to portfolio profitability.
Simply accepting that profitability will wax and wane with market cycles isn’t keeping up with the times. Though the length and intensity may change, markets will continue to cycle. Sophisticated carriers know that these cycles present not a threat to profits, but new opportunities for differentiation. Modern approaches to policy acquisition and retention are much more focused on individual risk pricing and selection that incorporate data analytics. The good news is that these data-driven carriers are much more in control of their own destiny, and less subject to market fluctuations as a result.
Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Bret Shroyer is the solutions architect at Valen Analytics, a provider of proprietary data, analytics and predictive modeling to help all insurance carriers manage and drive underwriting profitability. Bret identifies practical solutions for client success, identifying opportunities to bring tangible benefits from technical modeling.
The federal government is demanding better security for personal health data, and those operating health plans must react.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Cynthia Marcotte Stamer is board-certified in labor and employment law by the Texas Board of Legal Specialization, recognized as a top healthcare, labor and employment and ERISA/employee benefits lawyer for her decades of experience.
Early studies on using mammograms to screen for breast cancer were deeply flawed, largely because they can lead to over-diagnosis.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Tom Emerick is president of Emerick Consulting and cofounder of EdisonHealth and Thera Advisors. Emerick’s years with Wal-Mart Stores, Burger King, British Petroleum and American Fidelity Assurance have provided him with an excellent blend of experience and contacts.
To captivate customers, it isn't enough to just change the technology that they touch. You have to take a broad look at all systems.

 When developing for a multi-channel experience, it’s crucial to do lots of A/B testing – changing one variable at a time for a sample of customers, seeing how they react and incorporating those changes that produce better results. It’s also important to actually watch customers to see how they navigate a process – where they stop, where they start up again, where they get sidetracked, where they get confused. We’ve watched customers many times, and the results can be surprising enough to at least require considerable tinkering.
For example, with three releases each year, Salesforce has delivered 47 major releases since its inception. Each release is informed by learning from how users behave, adopt and use Salesforce’s features. As a result, more than 1,700 features have been sourced directly from Salesforce’s customer community. In insurance, Salesforce learns from more than 2,500 insurance customers. These continuing improvements happen in an agile fashion, and follow an iterative cycle of release, learn and improve.
The race to become a leading insurer that is able to attract, satisfy and retain customers is in full motion. Those insurers that can blend traditional channels and digital channels in a seamless way will lead the race, creating clear competitive advantage with the capabilities in place to capitalize on market disruption over the coming years.
The first two articles in this series are here and here. For the white paper from which these articles are adapted, click here.
When developing for a multi-channel experience, it’s crucial to do lots of A/B testing – changing one variable at a time for a sample of customers, seeing how they react and incorporating those changes that produce better results. It’s also important to actually watch customers to see how they navigate a process – where they stop, where they start up again, where they get sidetracked, where they get confused. We’ve watched customers many times, and the results can be surprising enough to at least require considerable tinkering.
For example, with three releases each year, Salesforce has delivered 47 major releases since its inception. Each release is informed by learning from how users behave, adopt and use Salesforce’s features. As a result, more than 1,700 features have been sourced directly from Salesforce’s customer community. In insurance, Salesforce learns from more than 2,500 insurance customers. These continuing improvements happen in an agile fashion, and follow an iterative cycle of release, learn and improve.
The race to become a leading insurer that is able to attract, satisfy and retain customers is in full motion. Those insurers that can blend traditional channels and digital channels in a seamless way will lead the race, creating clear competitive advantage with the capabilities in place to capitalize on market disruption over the coming years.
The first two articles in this series are here and here. For the white paper from which these articles are adapted, click here.
Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Bhuvan Thakur is a vice president within the Enterprise Cloud Services business for Capgemini in North America, UK and Asia-Pacific. Thakur has more than 18 years of consulting experience, primarily in the customer relationship management (CRM) and customer experience domain.

Jeff To is the insurance leader for Salesforce. He has led strategic innovation projects in insurance as part of Salesforce's Ignite program. Before that, To was a Lean Six Sigma black belt leading process transformation and software projects for IBM and PwC's financial services vertical.
Too often, data analysis is an unplanned art, with too many "rabbit warrens" being explored. A disciplined approach is required.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Paul Laughlin is the founder of Laughlin Consultancy, which helps companies generate sustainable value from their customer insight. This includes growing their bottom line, improving customer retention and demonstrating to regulators that they treat customers fairly.
A new breed of financially focused malware is continually mutating to avoid detection and is being aimed at 1.3 billion email addresses.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|
The Achilles heel is that systems design theory of the '80s and '90s was component-based. It made sense at the time; it doesn’t any more.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Brian Harrigan, CEO of InsurIQ, a provider of insurance technology solutions, has spent over 40 years in the insurance industry, helping agents and carriers manage the purchasing of insurance and personal protection products.