Finally, a bit of good news on ransomware: Federal investigators said Monday that they had recovered millions of dollars of the ransom that Colonial Pipeline paid to Russian hackers following their recent attack, which disrupted gasoline supplies up and down the East Coast.
The news may discourage ransomware hackers by showing them that they aren't as invincible as they think -- while they operate from countries that aren't likely to cooperate with international enforcement and take payment in cryptocurrency, U.S. investigators tracked the Colonial Pipeline ransom to a digital wallet and recovered much of it. The news also underscores FBI Director Christopher Wray's statement last week that ransomware attacks should be seen as terrorist activity that warrants a heavy response from law enforcement, suggesting that potential corporate targets and their insurers may receive much-needed help.
To understand where ransomware attacks and cyber insurance go from here, I sat down recently with Brian Brown, principal and consulting actuary at Milliman, and Paul Miskovich, consultant who has been working with Milliman on cyber issues. As you'll see, they offered a modicum of optimism but raised some tricky issues that both insurers and corporate clients will face -- and laid out some cyber threats that lie ahead even if ransomware starts to come under control.
Here is the conversation:
ITL:
When we started planning this conversation, there had just been a high-profile ransomware attack, the one that shut down Colonial Pipeline and greatly restricted the availability of gasoline on the East Coast for days. We’ve since had an attack on JBS, which is the world’s largest meat seller and which provides a quarter of the beef and a fifth of the pork consumed in the U.S. Now that awareness is finally rising for this long-festering problem, what happens next?
Paul Miskovich:
For companies and clients, the attacks will drive investment in cyber resiliency.
The guidance from U.S. regulators and law enforcement, which has been very consistent, is that paying ransoms encourages bad actors to accelerate crimes involving ransomware. The Office of Foreign Assets Control and the Financial Crimes Enforcement Network released advisories in October that warned of sanctions for victims who make ransomware payments. So, you're in a Catch-22 if you’re attacked. If you choose to pay, you may have to pay penalties. If you choose not to pay, you could suffer reputational harm and other financial losses from being shut down. So, the only correct thing to do is to invest more in cyber resiliency.
ITL:
My thesis has been that the insurance companies should play a major advisory role because they are experts or at least more expert than the individual clients, based on all the cases they are seeing. Is that a reasonable thought?
Paul Miskovich:
It is, but there are issues.
Insurance companies are also affected by the OFAC advisory, and they have issues in making payments. They will need to start investing in technology partners to be able to make ransomware payments, which typically are done in cryptocurrencies. Insurers will also have to work more closely with law enforcement, to avoid sanctions and penalties. With respect to clients, insurers are going to have to work much more closely on prevention and resiliency.
And then you end up with other issues. Hackers will use AI and algorithms that accelerate the pace of the attack and could release confidential information, meaning that victims need to pay the ransom fast. So, insurance companies are going to have to figure out assessment and payment methodologies that work a lot faster than they work now.
ITL:
Can intelligence and law-enforcement agencies like the FBI do more to spot attacks potentially coming from overseas and maybe even shut them down?
Paul Miskovich:
Agencies are going to have to increase their scale, because they don't have the necessary resources to address the growing cyber threat. There’s a whole criminal network behind ransomware that’s exchanging money in the form of cryptocurrencies, so law enforcement has to get to a level of sophistication that it can use blockchain and other technologies to track the flow and disrupt the perpetrators.
ITL:
What are all these threats doing to insurers and to rates?
Brian Brown:
From 2015 to 2020, premium growth for cyber insurance has been in excess of 25% a year, and the current cyber premium is about $2.3 billion a year. It’s possible that's understated, because carriers may not be reporting all of the cyber premium. Also, this is just premium written by U.S. domestic companies.
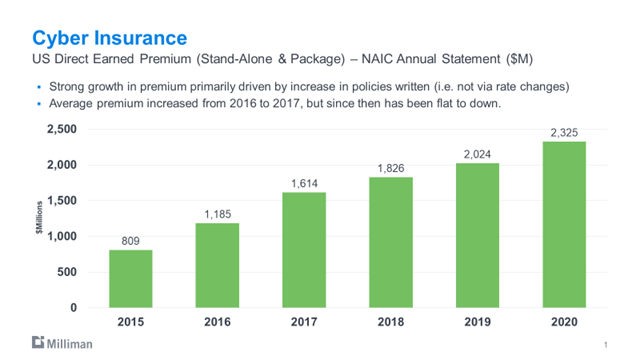
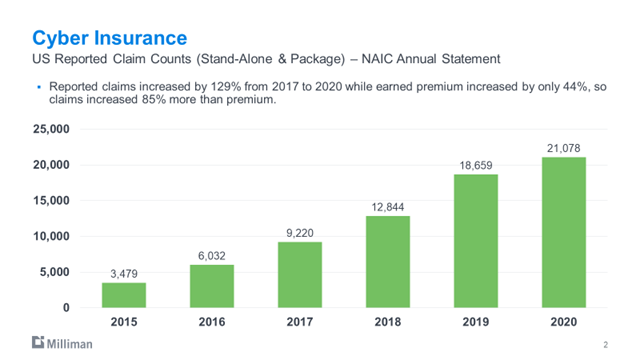
We started to see a big tick up in claims in 2019. The 2019-2020 claim activity has been more than double 2017.
Loss ratios were pretty favorable for stand-alone cyber policies from 2015 to 2018, below or close to 50%. But in 2020 the loss ratio was 73%. That's assuming that the carriers are perfectly reserving the exposure. We've looked at some other data for policies just written in 2020, and the indicated loss ratios, early on, may be much higher than 73%.
A lot of big companies have pretty tight security plans; the medium-sized companies not as much. So, there may be much heavier rate activity for the medium-sized companies. But the fundamental issue is, which insurers can determine new more robust variables that predict the likelihood of a cyber loss.
And, if you're insuring somebody, you want to provide risk management services to reduce their probability of a cyber event, whether that's providing courses to employees or software to IT departments to measure cyber resilience. You also really need a qualified staff to handle claims.
The predictions are that premiums will continue to grow well in excess of 25% annually for years to come. So, I think we're on the cutting edge of a great opportunity for a lot of insurance companies, if they're able to do it right.
ITL:
Do you want to speculate a bit on what the next threat will be, beyond ransomware?
Paul Miskovich:
I see three. The first one, undeniably, is the exploitation of cloud computing vulnerabilities. Next are the cyber security breaches originating from vulnerabilities in ecosystems, where the victim is provided services, especially web applications, through a third-party offsite server. That area of exposure is going to continue to increase. The other one is that the sophistication of exploits is increasing with artificial intelligence and self-learning algorithms. Denial of service attacks are becoming especially dynamic. The algorithms are quicker and more effective. The algorithm chooses one or more methods of attack using behavioral analysis of the network to try to figure out how to get through the defenses.
ITL:
On the theory that we should fight the next war, not the last one (as generals famously are said to do), are there particular things you would recommend that anyone in this ecosystem -- the clients, the insurers, the regulators or the investigative agencies -- should do to prepare us better for those next threats?
Paul Miskovich:
I feel that Congress should establish federal minimum cyber security standards for private businesses. And law enforcement and regulators should put forth information campaigns educating the public. Together, they will set a common basis of knowledge and preparation and will drive investment in cyber resiliency, while improving private companies’ responsiveness to quickly evolving threats.
As for critical infrastructure -- energy, transportation and healthcare -- I think they require much, much deeper resiliency planning.
We don't really know what the next attack will be, but if we all have the same baseline through training and standards, and we’re all sharing information, then our responses can be more effective.
Brian Brown:
We’re seeing a hard market now, but if we were to get one or several large events, in the $100 million to $1 billion range, we'd see an extremely hard market, and quite possibly capacity issues. So, some are looking at alternative capital sources to provide cyber coverage. We’re also seeing some MGAs and insurtechs actually doing the underwriting, which is likely to be a growing trend.
Paul Miskovich:
Many of the later entrants in the cyber market think it's more efficient to use specifically targeted, talented teams coming out of MGAs.
Brian Brown:
There are some additional benefits from the MGA relationship, because, if you're not happy with the performance of the portfolio, it's easier to exit. So, it's a quicker ramp up and an easier exit.
ITL:
Thanks to you both. This has been a great discussion.
Cheers,
Paul
P.S. Here are the articles I'd like to highlight from the past week:
Behavioral Science and Life Insurance
Carriers must fully grasp human biases and behaviors and harness technologies to improve health.
Ready for the Fully Connected Future?
The key for insurers is to think beyond a single transaction and be “partnership-ready,” which also means becoming “ecosystem-ready.”
The Promise of Predictive Models
Big data and AI will uncover insights that allow smart carriers to acquire the most profitable clients and avoid the worst.
Key to Transformation for Auto Claims
AI is critical to processing and assessing all inputs and removing friction. Yet AI alone cannot deliver transformation.
Auto Insurers Prep for Summer Driving
By taking steps now to update, optimize and digitize processes, insurers will be prepared to help customers through this likely difficult time.
Different Flavors of Transformation
Transformation and improvement are not the same, and insurers should use different approaches to the two types of innovation.





