Digital, data and core capabilities have changed dramatically over the last decade and continue to evolve rapidly. To help insurers track these capabilities and their progress, we created the Novarica New Normal 100 benchmark, which we’ve conducted for the last few years.
In this article, we’ll discuss the role of digital, data and core capabilities in key functional areas -- product development, marketing, distribution, underwriting, customer engagement, billing, claims and finance/operations -- and review our findings on the current state and near-term plans of insurers.
Product Development
Most insurers don’t think of digital as having a big impact on product development, but streamlining can have a real impact on speed to market. Considering digital distribution and underwriting during the product development process is also important.
Data and analytics have always been at the center of product development. As third-party data has become more abundant, and analytical tools and data management capabilities have become more advanced, product developers and actuaries can leverage new capabilities to optimize both pricing accuracy and ease of underwriting and distribution.
Products need to be instantiated into core processing systems to be offered and managed. Flexible core systems enable better product development and management.
See also: It’s Time to Accelerate Digital Change
The majority of P/C insurers report designing at least some products to be optimized for streamlined underwriting, omitting unnecessary questions and using pre-fill data. Use of machine learning in developing rating algorithms is still very uncommon, with fewer than 10% of insurers having any capabilities. However, more than 25% have current or planned pilots in this area.
Only about a third of life/annuity insurers have a digital workflow for product development. More than half are designing products to leverage the availability of pre-fill data. While only a third are currently using analytics to drive product design, an equal number are piloting that capability. A little more than a third have at least some centralized product modeling capabilities.
Marketing
With the exception of direct personal lines writers, few insurers have really advanced digital marketing capabilities—most of the attention in digital marketing is focused on distribution. Data and analytics are at the heart of marketing. Being able to profile target customers, model behavior and analyze effectiveness of marketing programs is important for engaging with potential customers. Insurers are even using existing data about prospects to “pre-underwrite” risk and offer price indications without engaging with customers. While this capability is not yet mature, a significant number of insurers report having some capabilities in this area.
Few P/C insurers see themselves having mature capabilities in any digital or data marketing area, but use of analytics and profiling is fairly widespread, with 30% of 50% of insurers reporting some capabilities. The most common area for planned pilots is customer profiling and modeling, with a quarter of insurers exploring this area further. Smaller insurers are less advanced in aggregate but have more current or planned pilots.
Among life/annuity insurers, household-level customer analysis is still unusual, but is a very common area of pilot activity. Customer profiling and behavior modeling is increasingly common, with more than a third of insurers reporting at least some capabilities.
Distribution
Distribution has been the focus of most insurers’ digital strategies, and there are many digital distribution capabilities that insurers should consider. This includes providing both information and transactional capabilities to distributors or end buyers via Web and mobile. Data capabilities in this area are a combination of interactive analytics to maximize the effectiveness of distribution channels and effective use of third-party data to streamline the buying experience. Core systems have a critical role to play in managing distribution forces and enabling rapid service to both distributors and customers.
Insurers have divergent digital capabilities to support their distributors. Fewer than half of P/C insurers have mobile new business, commissions or interactive sales materials. About half use pre-fill data to streamline application submission, and similar numbers offer quick quotes with minimal data entry. Use of analytics to drive next-best offer is rare, but about a third of larger insurers have current or planned pilots in this area.
Digital distribution maturity levels at life/annuity insurers are comparatively high. More than half of insurers report e-signature capabilities, mobile-optimized new business systems and interactive sales materials. Self-service licensing and appointments management is common at large insurers, but no midsize insurers report current capabilities. Insurers in both size classes report active pilots in this area.
Underwriting
While many insurers think of digital primarily in terms of external communications, both streamlining underwriter workflows and improving internal knowledge sharing depend on digital capabilities. Data and analytics capabilities are obviously important for underwriting, as well, and depend on core underwriting systems that support their workflows and models.
Data and analytics capabilities in underwriting are widespread, with more than two-thirds of large P/C insurers claiming some capabilities in nearly every area, including predictive scoring. But fewer than 10% claim mature functions. More than two-thirds of insurers report having paperless underwriting workflow capabilities, but fewer than half of those claim mature capabilities.
More than half of life/annuity insurers report at least some paperless underwriting workflows, and another quarter report current or planned pilots. Predictive scoring is also in use at more than a third of insurers, with more than 40% reporting pilot activity in this area.
Customer Engagement
Customer engagement is a major focus for insurers’ digital strategies. These cover engaging with customers via Web, mobile and social media or providing analytics-driven recommendations. Data and analytics-related capabilities in this area are closely related to those used in marketing. These involve both effective data consolidation and reporting as well as offline analytics to improve service levels and engagement.
Insurers continue to expand their digital customer engagement capabilities, but even basic functions like same-day email responses to customer inquiries are not universal. Only half of P/C insurers support self-service change requests or have mobile customer applications. Fewer than a quarter have online chat or co-browsing with clients, or offer policyholders a 360-degree view across different product sets.
Life/annuity insurers’ digital capabilities in customer engagement are uneven. Online chat is not widely deployed today, but more than half have current or planned pilots. While close to a quarter of insurers report mature customer mobile capabilities, more than one-third still do not have same-day e-mail response to inquiries. Online video and co-browsing with service representatives are still rare.
Analytics usage in customer engagement is also rare, with fewer than a quarter of life/annuity insurers reporting current capabilities in using analytics for retention modeling or service tiering.
Billing
Digital billing capabilities are all related to electronic communications and payments using current and emerging channels and payment mechanisms. Data capabilities are focused on analytics, both internal performance analytics and analytics to drive customer messaging, while insurers’ abilities to meet customer expectations in billing, which include consolidation and customization, are highly dependent on flexible core billing systems.
Electronic bill presentment and payment is widespread but still not universal, with only about 60% of P/C insurers supporting this capability. Credit card payments are also not universal. Using analytics to prevent premium leakage is in place at 30% to 40% of insurers, but more than a quarter of insurers are piloting this application of analytics.
Only about half of large life/annuity insurers report supporting electronic bill presentment and payment, and fewer than a third accept online or mobile credit card payments (although mail/phone card payments are more common). Analytics usage in billing is negligible, and large life/annuity insurers’ ability to customize billing schedules or present consolidated bills is very limited.
See also: Key Trends in Innovation (Parts 4, 5)
Claims
Applying digital capabilities to claims means streamlining communications across the value chain from claimants and adjusters to third-party service providers. Claims data and analytics capabilities are primarily focused on building and applying predictive models across multiple areas. Most of the digital and data/analytics capabilities involved in claims depend on core underwriting systems that support their workflows and models.
Claims is the area with the highest pilot activity among large P/C insurers. More than a third are piloting just about every digital and data/analytics capability, especially predictive fraud scoring and severity scoring. Core capabilities like skills-based routing and triaged straight-through processing are common among P/C insurers but not universal, and maturity levels are still relatively low.
About a quarter of life/annuity insurers are using predictive modeling for fraud scoring, and there are a handful of pilot programs in using analytics in claims areas. Digital capabilities like role-based third-party access are extremely limited, and few large insurers have or are investing in paperless claims processes. Skills-based routing of claims is fairly common.
Finance/Operations
While most insurers think about data and digital capabilities primarily in outward-facing roles, and most recent core investments focus on products and speed to market, insurers are also deploying technology-enabled capabilities to manage their finance and operations more effectively.
Capabilities include internal self-service, more advanced reporting and more flexible and powerful core systems that enable faster responses and better internal service levels. About half of P/C insurers report at least some current capabilities in this area. Larger insurers are generally more advanced, and pilot activity is low across the board.
Digital and data capabilities in finance and operations are increasingly common at life/annuity insurers, but still not universal. Nearly a third of insurers still are unable to allocate monthly P&Ls by product or channel, and more than two-thirds lack enterprise-wide customer data analytics capabilities.
Concluding Thoughts
While keeping an eye on the technology developments of tomorrow, insurers need to consider the capabilities available today and the impact of delaying deployment of those capabilities. Our research paints a picture of a continuing digital divide between have and have-not insurers, as well as a data divide and a core capabilities divide. In a market where growth is hard to come by, insurers need to develop better digital capabilities to serve customers and streamline processes among all stakeholders, better data and analytics capabilities to model risk and customer behavior and better core capabilities to support more agile processes and a more agile product portfolio.
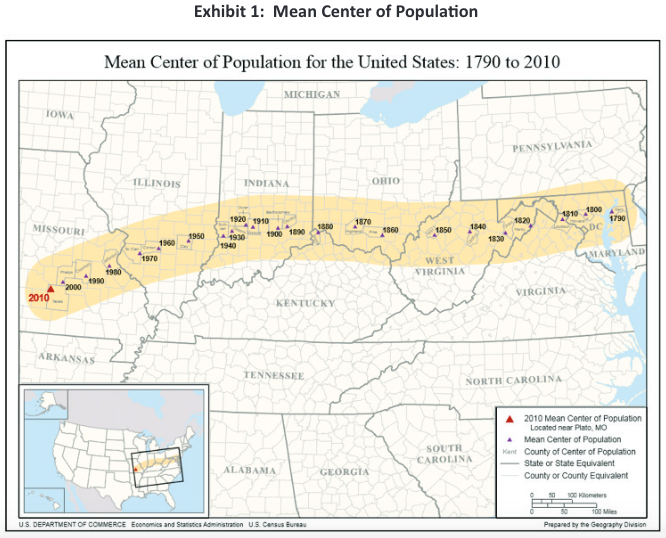 As the inset map shows, this is east and south of the geographic center of the U.S. The major population centers in the eastern half of the country pull it east. The major population centers in the south pull it south. More than 10% of the population is in one major southwestern state, California. Major metropolitan areas can be found throughout the country: San Francisco and Los Angeles in the Southwest, Dallas and Houston in the south Midwest, Chicago in the upper Midwest, Boston and New York in the northeastern part of the country, Atlanta and Miami in the Southeast. Why is this important?
More than 90% of the Canadian population lives within 100 miles of the U.S. border. The oft-touted Canadian system serves a population that is concentrated in a thin band of land. In a concentrated environment, it is possible to have a more efficient allocation of resources. In the Canadian provinces with significant rural populations (e.g., Alberta and Saskatchewan) the provinces use regional health authorities to take responsibility.
See also: A Road Map for Health Insurance
American Definition of Quality
Quality is difficult to universally define. Many times people say, “I know it when I see it” or, more importantly “I know it when I don’t see it.” Over the past 15 to 20 years, quality has been objectively defined, to the point that it is consistently measured across health systems. One of the best definitions of quality is “providing the right service, at the right time, to the right patient as efficiently as possible.” The American definition of quality usually includes a high degree of access and a significant sense of urgency.
Other countries do not see waiting as a deterioration in quality. In fact, queuing, or waiting lines, are accepted. The American ideal is getting healthcare now, not tomorrow, not next week or next year. Most Americans see waiting as a reduction in quality. Health systems that require pre-authorization or approval of referrals are frequently viewed as substandard because those systems create barriers that patients have to work through. In countries with socialized healthcare systems, patients regularly have to wait. Much of this wait is associated with fiscal limits within the system restricting the available resources. In the U.S., the excess capacity in the system almost always provides an adequate supply of healthcare resources, so the required waiting time is very limited.
The waiting line is caused by either quotas or specific budgets for specific procedures, producing a rigid form of rationing. In the U.S., waiting occurs when the physician was booked or the schedule was full. This queue is not a budget-driven constraint.
The U.S. healthcare system is recognized as one of the highest-quality in the world (e.g., high cancer screening rates). Although the quality of care is generally quite high, some of the measured outcomes suggest that the U.S. health system is not advancing as much as would be hoped. One example is the efforts to eliminate breast cancer. Screening for breast cancer is higher than it has ever been, but so is the rate of breast cancer. Perhaps improved detection has identified more cases.
Freedom of Choice
Americans value freedom of choice; they like to make decisions for themselves. Americans value going where they want to get care, choosing who they want to provide that care, oftentimes deciding what care they want and getting it when they want to get it. This has resulted in broader networks offering more choices than needed. This has resulted in higher-than-necessary utilization of specific services, including new technology. The need for freedom of choice has limited the effectiveness of care management programs. Freedom of choice combined with limited cost sharing results in expensive healthcare. One unfortunate consequence is the negative opinion that develops regarding any administrative process that limits freedom of choice. Programs that focus on limiting medically unnecessary care are accused of disrupting the physician/patient relationship.
Healthcare Resource Planning
In most states, there is very limited overall resource planning. At various times, some states have implemented certificate of need programs for specific types of providers. But, for the most part, there are no formal limits to the number of providers or types of providers. In most urban markets, there is an oversupply of providers. Rural markets are often plagued with a shortage. Some markets are so desperate for providers that significant compensation is offered to lure them.
Why is this important? Healthcare tends to be a market that fails to respond to traditional supply and demand economics. In the general economy, the greater the supply, the lesser the demand and the lower the prices. In healthcare, the higher the supply, the greater the induced demand and the continuation of higher prices. Informal studies suggest that utilization levels positively correlate with supply.
One of the reasons for escalating costs is the continued oversupply of healthcare providers. One of the best examples of effective resource planning is the approach implemented by Kaiser Foundation Health Plan. Kaiser carefully plans the supply of professional services based on a long-established staffing model. As the associated membership grows, they move from a combination of “nearby owned facilities” and “rented facilities” to “owned facilities.” Kaiser carefully manages the strategic transition to a “wholly owned delivery system” and manages the resources based on membership growth. Kaiser avoids excess capacity and maintains a cost-effective delivery system.
Countries with socialized healthcare systems are much more involved with resource planning than the U.S. The competitive nature of healthcare in the U.S. is much more focused on capturing market share than defining appropriate resources for a region. Less effective resource planning drives up the cost of care.
Wide Variations in Efficiency
The efficiency of regional healthcare systems varies significantly from one geographic market to another. Delivery system care patterns have emerged based on local needs, regional care practices and the extent of provider involvement in the financing of care. Markets like Portland, OR, have developed extremely efficient in-patient care patterns with a larger portion of their healthcare dollar going to professional providers. Other markets have emerged at the same time with much less efficient patterns. In-patient utilization patterns vary by more than 35% to 45%. Analyses show no clinical rationale to support the observed variation. The U.S. is one of the few countries exhibiting this level of variation. Experts generally concur that much of this variation is caused by personal physician preference.
Tax-Sheltered Benefits
The current tax-sheltered employee benefit approach emerged during the post-WWII era where employers were seeking creative ways to attract, hire and keep employees. The tax law enabled employers to write off the cost of benefits and provide their employees a valuable tax-sheltered employee benefit. The tax law provides this favorable status only to employer-sponsored programs. Individual health insurance benefit programs do not enjoy this same tax advantage. Tax reform efforts have considered eliminating this difference. Self-funded employer-sponsored benefit programs, including those involving labor union negotiations (i.e., Taft -Hartley plans) are also tax-advantaged.
This is an important issue when discussing transitions to alternative systems. What role will employers play? What about programs negotiated by labor unions? How will we unravel the tax-advantaged funding of healthcare costs by the employer?
Diverse Insurance and Claims Administration
The employee health benefit marketplace has grown significantly with a large variety of organizations targeting the effective administration of such programs. Merger/acquisition activity has transformed the marketplace into a handful of major players and a large number of regional players. Third party administrators (TPAs) are active in the market supporting the self-funded and self-administered benefit programs. The federal government provides government-sponsored coverage for the elderly and disabled (Medicare) and for beneficiaries in lower socio-economic levels (Medicaid). Many of these programs outsource the administration and risk taking to the private sector. Healthcare administration in the U.S. includes a significant private sector involvement. There is little uniformity between different health plans. There are limited standards to streamline the process.
Public/Private Sector Cost Shift
The U.S. healthcare system incorporates a significant cost shift between the government-sponsored programs and the private sector programs. The private sector pays a much higher amount for identical services than the public sector. Within the private sector, each carrier/health plan is required to negotiate payment rates, which can vary substantially from one carrier to the next. The variability in reimbursement increases administrative costs for both the providers and the health plans or administrators.
See also: Healthcare Debate Misses Key Point
Hesitancy to Declare Healthcare a Human Rights Issue
In the U.S., there has been a hesitancy to declare healthcare a human rights issue. In Canada, the Canada Health Care Act defines five principles:
As the inset map shows, this is east and south of the geographic center of the U.S. The major population centers in the eastern half of the country pull it east. The major population centers in the south pull it south. More than 10% of the population is in one major southwestern state, California. Major metropolitan areas can be found throughout the country: San Francisco and Los Angeles in the Southwest, Dallas and Houston in the south Midwest, Chicago in the upper Midwest, Boston and New York in the northeastern part of the country, Atlanta and Miami in the Southeast. Why is this important?
More than 90% of the Canadian population lives within 100 miles of the U.S. border. The oft-touted Canadian system serves a population that is concentrated in a thin band of land. In a concentrated environment, it is possible to have a more efficient allocation of resources. In the Canadian provinces with significant rural populations (e.g., Alberta and Saskatchewan) the provinces use regional health authorities to take responsibility.
See also: A Road Map for Health Insurance
American Definition of Quality
Quality is difficult to universally define. Many times people say, “I know it when I see it” or, more importantly “I know it when I don’t see it.” Over the past 15 to 20 years, quality has been objectively defined, to the point that it is consistently measured across health systems. One of the best definitions of quality is “providing the right service, at the right time, to the right patient as efficiently as possible.” The American definition of quality usually includes a high degree of access and a significant sense of urgency.
Other countries do not see waiting as a deterioration in quality. In fact, queuing, or waiting lines, are accepted. The American ideal is getting healthcare now, not tomorrow, not next week or next year. Most Americans see waiting as a reduction in quality. Health systems that require pre-authorization or approval of referrals are frequently viewed as substandard because those systems create barriers that patients have to work through. In countries with socialized healthcare systems, patients regularly have to wait. Much of this wait is associated with fiscal limits within the system restricting the available resources. In the U.S., the excess capacity in the system almost always provides an adequate supply of healthcare resources, so the required waiting time is very limited.
The waiting line is caused by either quotas or specific budgets for specific procedures, producing a rigid form of rationing. In the U.S., waiting occurs when the physician was booked or the schedule was full. This queue is not a budget-driven constraint.
The U.S. healthcare system is recognized as one of the highest-quality in the world (e.g., high cancer screening rates). Although the quality of care is generally quite high, some of the measured outcomes suggest that the U.S. health system is not advancing as much as would be hoped. One example is the efforts to eliminate breast cancer. Screening for breast cancer is higher than it has ever been, but so is the rate of breast cancer. Perhaps improved detection has identified more cases.
Freedom of Choice
Americans value freedom of choice; they like to make decisions for themselves. Americans value going where they want to get care, choosing who they want to provide that care, oftentimes deciding what care they want and getting it when they want to get it. This has resulted in broader networks offering more choices than needed. This has resulted in higher-than-necessary utilization of specific services, including new technology. The need for freedom of choice has limited the effectiveness of care management programs. Freedom of choice combined with limited cost sharing results in expensive healthcare. One unfortunate consequence is the negative opinion that develops regarding any administrative process that limits freedom of choice. Programs that focus on limiting medically unnecessary care are accused of disrupting the physician/patient relationship.
Healthcare Resource Planning
In most states, there is very limited overall resource planning. At various times, some states have implemented certificate of need programs for specific types of providers. But, for the most part, there are no formal limits to the number of providers or types of providers. In most urban markets, there is an oversupply of providers. Rural markets are often plagued with a shortage. Some markets are so desperate for providers that significant compensation is offered to lure them.
Why is this important? Healthcare tends to be a market that fails to respond to traditional supply and demand economics. In the general economy, the greater the supply, the lesser the demand and the lower the prices. In healthcare, the higher the supply, the greater the induced demand and the continuation of higher prices. Informal studies suggest that utilization levels positively correlate with supply.
One of the reasons for escalating costs is the continued oversupply of healthcare providers. One of the best examples of effective resource planning is the approach implemented by Kaiser Foundation Health Plan. Kaiser carefully plans the supply of professional services based on a long-established staffing model. As the associated membership grows, they move from a combination of “nearby owned facilities” and “rented facilities” to “owned facilities.” Kaiser carefully manages the strategic transition to a “wholly owned delivery system” and manages the resources based on membership growth. Kaiser avoids excess capacity and maintains a cost-effective delivery system.
Countries with socialized healthcare systems are much more involved with resource planning than the U.S. The competitive nature of healthcare in the U.S. is much more focused on capturing market share than defining appropriate resources for a region. Less effective resource planning drives up the cost of care.
Wide Variations in Efficiency
The efficiency of regional healthcare systems varies significantly from one geographic market to another. Delivery system care patterns have emerged based on local needs, regional care practices and the extent of provider involvement in the financing of care. Markets like Portland, OR, have developed extremely efficient in-patient care patterns with a larger portion of their healthcare dollar going to professional providers. Other markets have emerged at the same time with much less efficient patterns. In-patient utilization patterns vary by more than 35% to 45%. Analyses show no clinical rationale to support the observed variation. The U.S. is one of the few countries exhibiting this level of variation. Experts generally concur that much of this variation is caused by personal physician preference.
Tax-Sheltered Benefits
The current tax-sheltered employee benefit approach emerged during the post-WWII era where employers were seeking creative ways to attract, hire and keep employees. The tax law enabled employers to write off the cost of benefits and provide their employees a valuable tax-sheltered employee benefit. The tax law provides this favorable status only to employer-sponsored programs. Individual health insurance benefit programs do not enjoy this same tax advantage. Tax reform efforts have considered eliminating this difference. Self-funded employer-sponsored benefit programs, including those involving labor union negotiations (i.e., Taft -Hartley plans) are also tax-advantaged.
This is an important issue when discussing transitions to alternative systems. What role will employers play? What about programs negotiated by labor unions? How will we unravel the tax-advantaged funding of healthcare costs by the employer?
Diverse Insurance and Claims Administration
The employee health benefit marketplace has grown significantly with a large variety of organizations targeting the effective administration of such programs. Merger/acquisition activity has transformed the marketplace into a handful of major players and a large number of regional players. Third party administrators (TPAs) are active in the market supporting the self-funded and self-administered benefit programs. The federal government provides government-sponsored coverage for the elderly and disabled (Medicare) and for beneficiaries in lower socio-economic levels (Medicaid). Many of these programs outsource the administration and risk taking to the private sector. Healthcare administration in the U.S. includes a significant private sector involvement. There is little uniformity between different health plans. There are limited standards to streamline the process.
Public/Private Sector Cost Shift
The U.S. healthcare system incorporates a significant cost shift between the government-sponsored programs and the private sector programs. The private sector pays a much higher amount for identical services than the public sector. Within the private sector, each carrier/health plan is required to negotiate payment rates, which can vary substantially from one carrier to the next. The variability in reimbursement increases administrative costs for both the providers and the health plans or administrators.
See also: Healthcare Debate Misses Key Point
Hesitancy to Declare Healthcare a Human Rights Issue
In the U.S., there has been a hesitancy to declare healthcare a human rights issue. In Canada, the Canada Health Care Act defines five principles:
















