A ransomware breach can be devastating for insurance providers, both in financial terms and in terms of the companies' reputation.
With ransomware attacks on the rise and growing in sophistication, it is no longer enough to have a contingency plan in place if the worst happens; forward-thinking providers are looking at ways to prevent the next data breach before it can result in harmful media coverage and a class action lawsuit.
That conversation should not be based in the IT department. Move it up to the C-suite level, where the focus is inherently directed toward the core objectives of asset protection and risk management.
A systems review for vulnerabilities from unpatched software or password attacks should be on the agenda, but do not overlook the way in which most ransomware is now delivered—through phishing emails distributed to all of your personnel, from the CEO to the newly hired junior underwriter.
Phishing emails? Like those old Nigerian prince scams? Hardly. By combining the capabilities of artificial intelligence (AI) with the voluminous amount of personal identifying information now easily accessible about all of us online, hackers can create personalized emails capable of fooling even the most vigilant employees.
This is how phishing used to look:
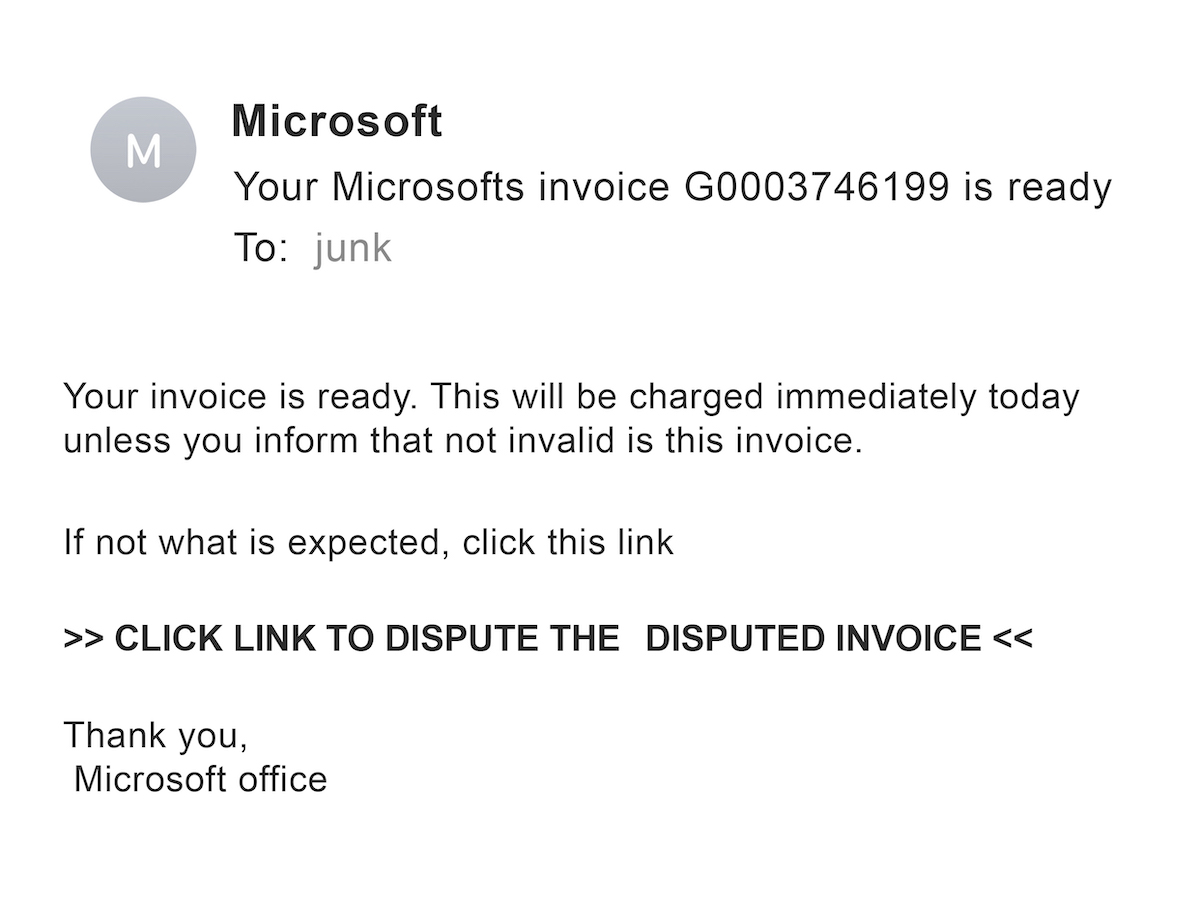
Surprisingly, even these types of emails still claim thousands of victims every year. But the current state of phishing can create emails like this:
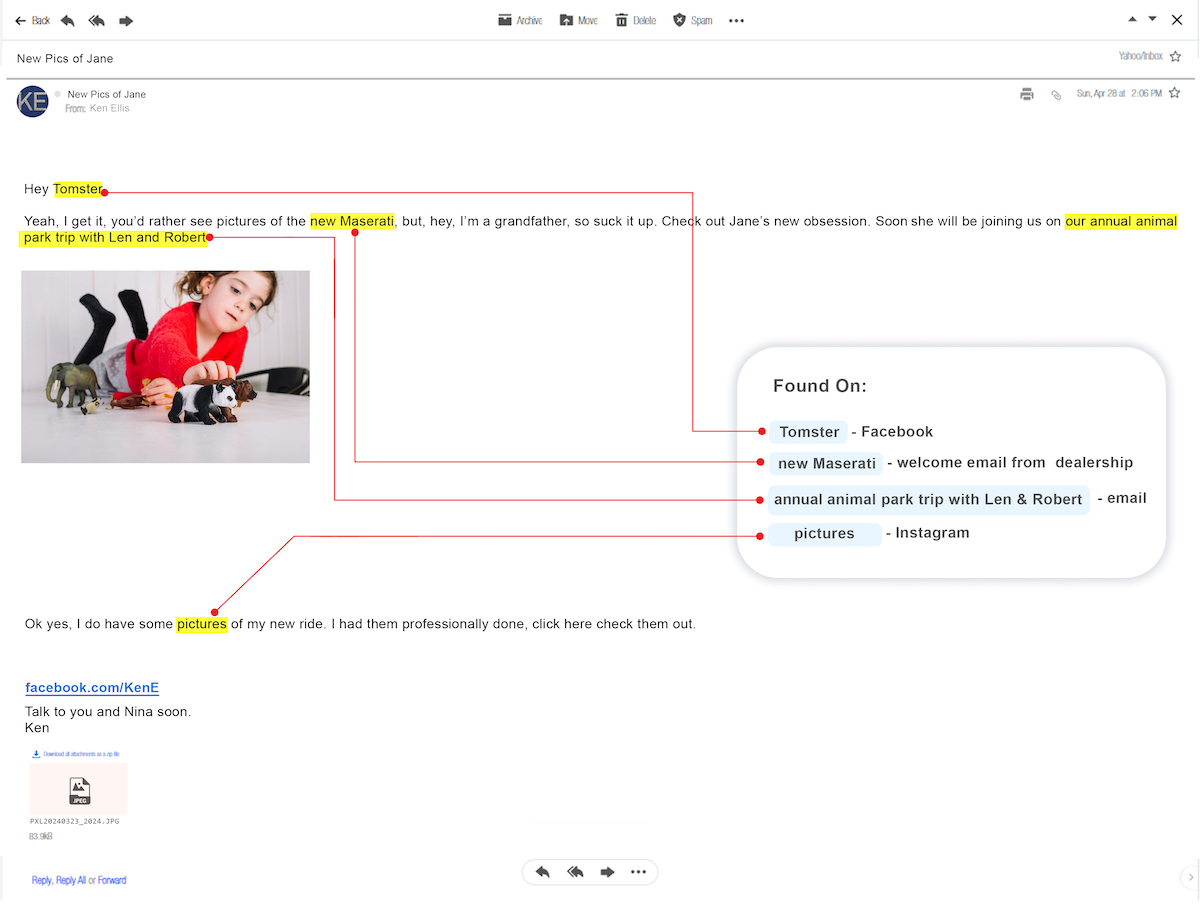
This email greets the recipient with a nickname commonly used by his friends and family. It was apparently sent by someone he knows and includes a photo and other personal details. The sender’s email address might be different, but given the preponderance of evidence that this is genuine, that difference could be attributed to the sender's changing email providers—if it is even noticed at all.
What would happen if enough information were found about 100 of your employees to create an email like this? One financial organization ran a penetration test and found that phishing emails like this one routinely averaged a 4% click-through rate, with half of those who clicked also downloading a malicious payload. That means for every 100 employees at your company, four are potential phishing victims. And all it takes is one click from one work account to compromise your systems.
How Do Hackers Obtain Private Information?
It’s easier than you might think. There are more than 250 data brokers that specialize in collecting personal identifying information on everyone, and sharing or selling access to that content to any interested party.
The potential pools of content sources that can be accessed are seemingly endless: news articles, public records, property ownership documents, Google Street View photos, high school/college records, community events, social media. During COVID, data brokers paid restaurants, then desperate to survive with empty dining rooms, to share whatever customer information they collected from apps, loyalty programs and food delivery orders.
In addition to personal and demographic data, organizations are also now gathering information on our opinions and behavior that can be leveraged to sell more products and services – and if data brokers want that content, as well, they are welcome to it.
See also: A Resurgence in Credit Card Fraud
Protect Your Company – By Protecting Your Personnel
Ransomware gangs achieved an alarming 56% increase in victims worldwide in 2023, despite greater awareness of the risk and despite servers having been hardened to resist infiltration. And early indications suggest that 2024 may be even worse. Imagine having to send the dreaded email to policyholders acknowledging that their personal information may have been acquired by hackers, access made possible in part because of one employee’s Instagram post about his trip to the Grand Canyon.
Trying to control the flow and exchange of information online to prevent such an attack may seem like an impossible task – like putting toothpaste back in the tube. But it can be done, and focusing on that objective now is preferable to dealing with the cost of restoring IT systems after a breach, providing credit monitoring and identity theft protection to victims and coping with the negative publicity and the class action lawsuit.
The plan starts with education. While every insurance organization likely provides guidance on recognizing the common signatures of phishing emails and texts, intensifying these efforts may be necessary to make personnel aware of the enhanced capabilities of AI-generated emails, and how vigilance is now more important than ever. Anything that looks even slightly suspicious should be questioned and reported.
Consider providing employees with a corporate account that monitors and removes personal information online. Some focus only on data brokers and people finder websites, where this content is most commonly found. Others will extend their search across the breadth of the internet to locate the kind of information that hackers exploit, and to make sure it comes down. Such services can cost as little as a few dollars per employee per year.
Once that content is removed, there are ways to prevent new content from showing up; tools such as a VPN and VoIP numbers can replace authentic information (i.e. phone numbers, online search and browsing history) with content that cannot be traced back to an individual user.
Not every organization will take these steps, which gives those that do an advantage because hackers, regardless of whatever IT skills they have acquired for their trade, are also lazy. They seek targets where the most content on the most individuals can be accessed and weaponized. If enough details about your personnel cannot be easily collected for a phishing attack that is likely to succeed, they will turn their attention elsewhere.
See also: Are You Fraud-Friendly?
An Ounce of Prevention…
Cyberattacks are on the rise across all industries, but the financial sector, including insurance organizations, is particularly vulnerable to a wide range of threats. The reason is obvious: hackers know these targets have access to millions of dollars in funds and provide critical services that many people rely on. They also see a high likelihood that victims will pay the ransom quickly to restore access. A 2023 survey from Sophos found that nearly half of those organizations that were hit chose to pay quickly.
In 2023, financial organizations had to invest an average of $2.2 million to fully recover from an attack, plus what could be millions more in legal fees.
By increasing awareness of the challenge of phishing – with both your personnel and your vendors – and reducing access to personal identifying information, it is possible to keep these AI-enhanced attacks from claiming your organization as their next victim.






