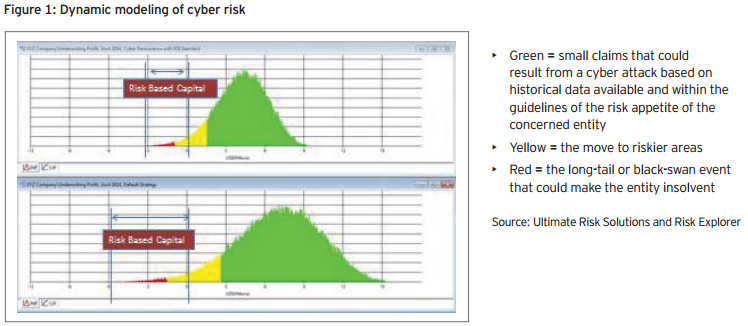
 The bottom graph shows the situation prior to reinsurance, where small claims are aggregated and a long tail cuts into the companies’ risk-based capital limits. The top graph shows a leaner risk situation after the application of reinsurance, bringing it back in the comfort zone.
The standard deviation process will depend on how the regulator views cyber risk and solvency. Currently, solvency models are geared on average to a 1-in-200-year event, which may be suitable for earthquake and other peril risks but is likely to be different for cyber risks and to vary by country risk appetite.
Other risk transfer mechanisms. In addition to reinsurance, cyber captives are used to address continuing risk. A point worth noting is the potential to mathematically create a “cyber index” in the same manner that weather and stock market indices appear in the macroeconomic models representing market risk exposure correlation to other enterprise risks. This cyber index could be created from the data patterns of the cyber catastrophe models and other data and then used as a threshold to trigger a data breach claims process following notification of a data breach.
Special-purpose vehicles (SPVs). This risk transfer approach is used in conjunction with capital market investors and sponsors, and it is similar to the catastrophe bond investments that protect countries from earthquake risk. It creates a bond shared by government and private industry to pay and share claims by loss bands in the event of a large or black-swan event. While these partnerships are very effective, such bonds often have a 10-year span, and a shorter life-span vehicle will be more suitable to cyber.
Sidecars. For natural catastrophes, these two-year vehicles have been referred to as sidecars, an SPV derivative of a captive where investors invest in a risk via A-rated hedge funds. If the event has not taken place within a given time frame, investors receive their money back with interest. This makes cyber risk part of an uncorrelated portfolio investment for chief investment officers. They can also base investment on the severity level of the attack, so investments are not lost on all events.
It will take time for this SPV approach to evolve over reinsurance and captives, but with good data quality, proper event models, ratings and adoption of KSI and other standards in the IT space, the capability to use capital markets to risk-transfer cyber risks will emerge. Data integrity standards would increase investor confidence in such SPVs.
For the full report on which this article is based, click here.
The bottom graph shows the situation prior to reinsurance, where small claims are aggregated and a long tail cuts into the companies’ risk-based capital limits. The top graph shows a leaner risk situation after the application of reinsurance, bringing it back in the comfort zone.
The standard deviation process will depend on how the regulator views cyber risk and solvency. Currently, solvency models are geared on average to a 1-in-200-year event, which may be suitable for earthquake and other peril risks but is likely to be different for cyber risks and to vary by country risk appetite.
Other risk transfer mechanisms. In addition to reinsurance, cyber captives are used to address continuing risk. A point worth noting is the potential to mathematically create a “cyber index” in the same manner that weather and stock market indices appear in the macroeconomic models representing market risk exposure correlation to other enterprise risks. This cyber index could be created from the data patterns of the cyber catastrophe models and other data and then used as a threshold to trigger a data breach claims process following notification of a data breach.
Special-purpose vehicles (SPVs). This risk transfer approach is used in conjunction with capital market investors and sponsors, and it is similar to the catastrophe bond investments that protect countries from earthquake risk. It creates a bond shared by government and private industry to pay and share claims by loss bands in the event of a large or black-swan event. While these partnerships are very effective, such bonds often have a 10-year span, and a shorter life-span vehicle will be more suitable to cyber.
Sidecars. For natural catastrophes, these two-year vehicles have been referred to as sidecars, an SPV derivative of a captive where investors invest in a risk via A-rated hedge funds. If the event has not taken place within a given time frame, investors receive their money back with interest. This makes cyber risk part of an uncorrelated portfolio investment for chief investment officers. They can also base investment on the severity level of the attack, so investments are not lost on all events.
It will take time for this SPV approach to evolve over reinsurance and captives, but with good data quality, proper event models, ratings and adoption of KSI and other standards in the IT space, the capability to use capital markets to risk-transfer cyber risks will emerge. Data integrity standards would increase investor confidence in such SPVs.
For the full report on which this article is based, click here.How to Apply ERM to Cyber Risks
Insurance and reinsurance are not alternatives to ERM; cyber risks must be assessed and mitigated like all other risks.

 The bottom graph shows the situation prior to reinsurance, where small claims are aggregated and a long tail cuts into the companies’ risk-based capital limits. The top graph shows a leaner risk situation after the application of reinsurance, bringing it back in the comfort zone.
The standard deviation process will depend on how the regulator views cyber risk and solvency. Currently, solvency models are geared on average to a 1-in-200-year event, which may be suitable for earthquake and other peril risks but is likely to be different for cyber risks and to vary by country risk appetite.
Other risk transfer mechanisms. In addition to reinsurance, cyber captives are used to address continuing risk. A point worth noting is the potential to mathematically create a “cyber index” in the same manner that weather and stock market indices appear in the macroeconomic models representing market risk exposure correlation to other enterprise risks. This cyber index could be created from the data patterns of the cyber catastrophe models and other data and then used as a threshold to trigger a data breach claims process following notification of a data breach.
Special-purpose vehicles (SPVs). This risk transfer approach is used in conjunction with capital market investors and sponsors, and it is similar to the catastrophe bond investments that protect countries from earthquake risk. It creates a bond shared by government and private industry to pay and share claims by loss bands in the event of a large or black-swan event. While these partnerships are very effective, such bonds often have a 10-year span, and a shorter life-span vehicle will be more suitable to cyber.
Sidecars. For natural catastrophes, these two-year vehicles have been referred to as sidecars, an SPV derivative of a captive where investors invest in a risk via A-rated hedge funds. If the event has not taken place within a given time frame, investors receive their money back with interest. This makes cyber risk part of an uncorrelated portfolio investment for chief investment officers. They can also base investment on the severity level of the attack, so investments are not lost on all events.
It will take time for this SPV approach to evolve over reinsurance and captives, but with good data quality, proper event models, ratings and adoption of KSI and other standards in the IT space, the capability to use capital markets to risk-transfer cyber risks will emerge. Data integrity standards would increase investor confidence in such SPVs.
For the full report on which this article is based, click here.
The bottom graph shows the situation prior to reinsurance, where small claims are aggregated and a long tail cuts into the companies’ risk-based capital limits. The top graph shows a leaner risk situation after the application of reinsurance, bringing it back in the comfort zone.
The standard deviation process will depend on how the regulator views cyber risk and solvency. Currently, solvency models are geared on average to a 1-in-200-year event, which may be suitable for earthquake and other peril risks but is likely to be different for cyber risks and to vary by country risk appetite.
Other risk transfer mechanisms. In addition to reinsurance, cyber captives are used to address continuing risk. A point worth noting is the potential to mathematically create a “cyber index” in the same manner that weather and stock market indices appear in the macroeconomic models representing market risk exposure correlation to other enterprise risks. This cyber index could be created from the data patterns of the cyber catastrophe models and other data and then used as a threshold to trigger a data breach claims process following notification of a data breach.
Special-purpose vehicles (SPVs). This risk transfer approach is used in conjunction with capital market investors and sponsors, and it is similar to the catastrophe bond investments that protect countries from earthquake risk. It creates a bond shared by government and private industry to pay and share claims by loss bands in the event of a large or black-swan event. While these partnerships are very effective, such bonds often have a 10-year span, and a shorter life-span vehicle will be more suitable to cyber.
Sidecars. For natural catastrophes, these two-year vehicles have been referred to as sidecars, an SPV derivative of a captive where investors invest in a risk via A-rated hedge funds. If the event has not taken place within a given time frame, investors receive their money back with interest. This makes cyber risk part of an uncorrelated portfolio investment for chief investment officers. They can also base investment on the severity level of the attack, so investments are not lost on all events.
It will take time for this SPV approach to evolve over reinsurance and captives, but with good data quality, proper event models, ratings and adoption of KSI and other standards in the IT space, the capability to use capital markets to risk-transfer cyber risks will emerge. Data integrity standards would increase investor confidence in such SPVs.
For the full report on which this article is based, click here.




