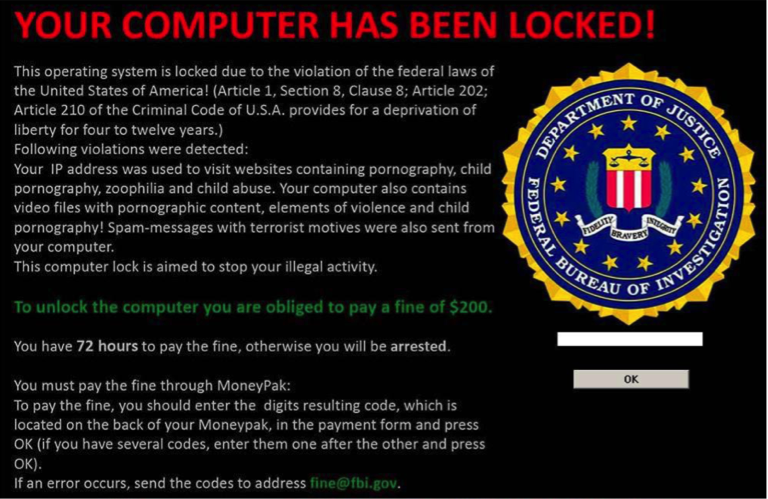
Ransomware: Your Money or Your Data!
Ransomware, which "kidnaps" firms' or individuals' data and demands payment for its release, is becoming increasingly common.


Ransomware, which "kidnaps" firms' or individuals' data and demands payment for its release, is becoming increasingly common.


Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Laura Zaroski is the vice president of management and employment practices liability at Socius Insurance Services. As an attorney with expertise in employment practices liability insurance, in addition to her role as a producer, Zaroski acts as a resource with respect to Socius' employment practices liability book of business.