How to Measure 'Vital Signs' for Cyber Risk
Many cybersecurity practitioners lack the jargon-free communication skills to present a clear picture of rising cyber exposures.

Many cybersecurity practitioners lack the jargon-free communication skills to present a clear picture of rising cyber exposures.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Byron Acohido is a business journalist who has been writing about cybersecurity and privacy since 2004, and currently blogs at LastWatchdog.com.
The shift to collaborate, rather than compete, with technology start-ups is gathering pace throughout the financial services industry.

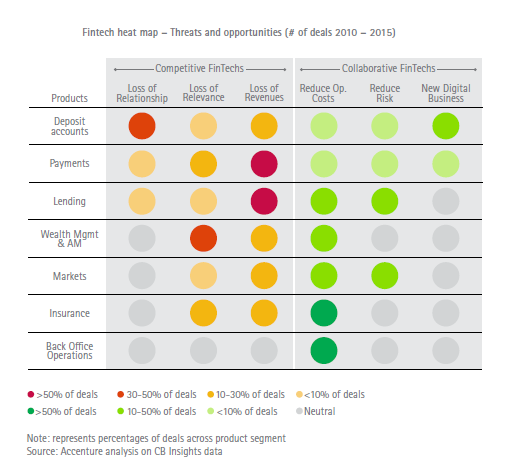 This trend is only beginning to affect the insurance industry. But as the InsurTech sector grows it will become much stronger.
Increasing cooperation between insurers and new technology firms is a sure sign of the growing maturity of the InsurTech sector. Many major carriers no longer worry that InsurTech firms might erode their business. Instead, they’re eager to benefit from the new insights, attitudes and technology they bring to the industry.
See also: Blockchain Technology and Insurance
The benefits of collaborating with InsurTech firms can be compelling and include:
This trend is only beginning to affect the insurance industry. But as the InsurTech sector grows it will become much stronger.
Increasing cooperation between insurers and new technology firms is a sure sign of the growing maturity of the InsurTech sector. Many major carriers no longer worry that InsurTech firms might erode their business. Instead, they’re eager to benefit from the new insights, attitudes and technology they bring to the industry.
See also: Blockchain Technology and Insurance
The benefits of collaborating with InsurTech firms can be compelling and include:
Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

John Cusano is Accenture’s senior managing director of global insurance. He is responsible for setting the industry group's overall vision, strategy, investment priorities and client relationships. Cusano joined Accenture in 1988 and has held a number of leadership roles in Accenture’s insurance industry practice.
Because of demands for adaptability, this is the first year that a majority of new core systems will not be deployed on-premise.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Karen Furtado, a partner at SMA, is a recognized industry expert in the core systems space. Given her exceptional knowledge of policy administration, rating, billing and claims, insurers seek her unparalleled knowledge in mapping solutions to business requirements and IT needs.
The author gets caught in a maze after finding he is at severe risk of glaucoma and must act immediately or lose his eyesight.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Dan Miller is president of Daniel R. Miller, MPH Consulting. He specializes in healthcare-cost containment, absence-management best practices (STD, LTD, FMLA and workers' comp), integrated disability management and workers’ compensation managed care.
Putting models into production is the fun part -- but requires not only testing but also a plan for monitoring and updating as time goes on.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

John Johansen is a senior vice president at Majesco. He leads the company's data strategy and business intelligence consulting practice areas. Johansen consults to the insurance industry on the effective use of advanced analytics, data warehousing, business intelligence and strategic application architectures.
Despite the crash and considerable trepidation, the author soon found himself trusting his Tesla to drive while he attended to email.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Vivek Wadhwa is a fellow at Arthur and Toni Rembe Rock Center for Corporate Governance, Stanford University; director of research at the Center for Entrepreneurship and Research Commercialization at the Pratt School of Engineering, Duke University; and distinguished fellow at Singularity University.
Start-ups such as LifeDrip and Smart Asset are going after distribution, product, client experience, speed, productivity and more.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Amy Radin is a transformation strategist, a scholar-practitioner at Columbia University and an executive adviser.
She partners with senior executives to navigate complex organizational transformations, bringing fresh perspectives shaped by decades of experience across regulated industries and emerging technology landscapes. As a strategic adviser, keynote speaker and workshop facilitator, she helps leaders translate ambitious visions into tangible results that align with evolving stakeholder expectations.
At Columbia University's School of Professional Studies, Radin serves as a scholar-practitioner, where she designed and teaches strategic advocacy in the MS Technology Management program. This role exemplifies her commitment to bridging academic insights with practical business applications, particularly crucial as organizations navigate the complexities of Industry 5.0.
Her approach challenges traditional change management paradigms, introducing frameworks that embrace the realities of today's business environment – from AI and advanced analytics to shifting workforce dynamics. Her methodology, refined through extensive corporate leadership experience, enables executives to build the capabilities needed to drive sustainable transformation in highly regulated environments.
As a member of the Fast Company Executive Board and author of the award-winning book, "The Change Maker's Playbook: How to Seek, Seed and Scale Innovation in Any Company," Radin regularly shares insights that help leaders reimagine their approach to organizational change. Her thought leadership draws from both her scholarly work and hands-on experience implementing transformative initiatives in complex business environments.
Previously, she held senior roles at American Express, served as chief digital officer and one of the corporate world’s first chief innovation officers at Citi and was chief marketing officer at AXA (now Equitable) in the U.S.
Radin holds degrees from Wesleyan University and the Wharton School.
To explore collaboration opportunities or learn more about her work, visit her website or connect with her on LinkedIn.
Life insurance, long a laggard, presents three main opportunities for innovation, and there are signs of, well, life.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Amy Radin is a transformation strategist, a scholar-practitioner at Columbia University and an executive adviser.
She partners with senior executives to navigate complex organizational transformations, bringing fresh perspectives shaped by decades of experience across regulated industries and emerging technology landscapes. As a strategic adviser, keynote speaker and workshop facilitator, she helps leaders translate ambitious visions into tangible results that align with evolving stakeholder expectations.
At Columbia University's School of Professional Studies, Radin serves as a scholar-practitioner, where she designed and teaches strategic advocacy in the MS Technology Management program. This role exemplifies her commitment to bridging academic insights with practical business applications, particularly crucial as organizations navigate the complexities of Industry 5.0.
Her approach challenges traditional change management paradigms, introducing frameworks that embrace the realities of today's business environment – from AI and advanced analytics to shifting workforce dynamics. Her methodology, refined through extensive corporate leadership experience, enables executives to build the capabilities needed to drive sustainable transformation in highly regulated environments.
As a member of the Fast Company Executive Board and author of the award-winning book, "The Change Maker's Playbook: How to Seek, Seed and Scale Innovation in Any Company," Radin regularly shares insights that help leaders reimagine their approach to organizational change. Her thought leadership draws from both her scholarly work and hands-on experience implementing transformative initiatives in complex business environments.
Previously, she held senior roles at American Express, served as chief digital officer and one of the corporate world’s first chief innovation officers at Citi and was chief marketing officer at AXA (now Equitable) in the U.S.
Radin holds degrees from Wesleyan University and the Wharton School.
To explore collaboration opportunities or learn more about her work, visit her website or connect with her on LinkedIn.
"The synthetic, opium-like drugs were so potent that six of the agents became ill after handling them. One fell into a coma."

Last spring, Chinese customs agents seized 70 kilograms of the narcotics fentanyl and acetyl fentanyl hidden in a cargo container for Mexico. The synthetic opium-like drugs were so potent that six of the agents became ill after handling them. One fell into a coma.The article goes on to describe how fentanyl often is disguised as hydrocodone and Xanax on the black market -- dangerous drugs by themselves but not nearly as potent or fatal as fentanyl. Because China does not regulate fentanyl or analogs used to create fentanyl, there is a significant financial incentive for the drug dealers -- $810 of materials can create 25 grams of fentanyl and yield as much as $800,000 in pills sold on the black market. See also: Opioids Are the Opiates of the Masses According to the Canadian Globe's expose on the issue (an excellent look at the black market), accessing fentanyl can be as easy as "Sign up for an account, choose a method of payment, and receive the package in three to four business days." Reinforcing the financial model: "A kilogram ordered over the internet – an amount equal in weight to a medium-sized cantaloupe – sells on the street in Calgary for $20 million, making it a drug dealer’s dream." So, fentanyl is a problem. It's 25 to 50 times more potent than morphine. It's highly addictive. It's available fairly easily on the black market. And it is prescribed by doctors. Way too often. Approved by the FDA and on script pads supplied by the DEA, its federal legitimacy adds to the lack of stigma associated with use. Which is one reason why I think Prince could rationalize his use. A doctor likely prescribed it for his chronic pain -- and other patients fall into that same trap (with fentanyl and other dangerous prescription drugs). According to the FDA's own warnings (as reported on drugs.com):
Because of the risks of addiction, abuse and misuse with opioids, even at recommended doses, and because of the greater risks of overdose and death with extended-release opioid formulations, reserve Fentanyl Transdermal system for use in patients for whom alternative treatment options (e.g., non-opioid analgesics or immediate-release opioids) are ineffective, not tolerated or would be otherwise inadequate to provide sufficient management of pain.See also: How to Help Reverse the Opioid Epidemic In my opinion, fentanyl should be used to help people die with dignity during end-of-life care. Period. It's that dangerous. And yet we see it being prescribed, used and paid for. Month. After. Month. If you are prescribing fentanyl: Why? If you are being prescribed fentanyl: Why? If you are paying for someone's fentanyl: Why? Too many people are overdosing and dying not to ask a simple question: Why?
Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Mark Pew is a senior vice president at Prium. He is an expert in workers' compensation medical management, with a focus on prescription drug management. Areas of expertise include: abuse and misuse of opioids and other prescription drugs; managing prescription drug utilization and cost; and best practices for weaning people off dangerous drug regimens.
Spending on InsurTech looks set to surge: What is your strategy to stay abreast of the new opportunities and threats?

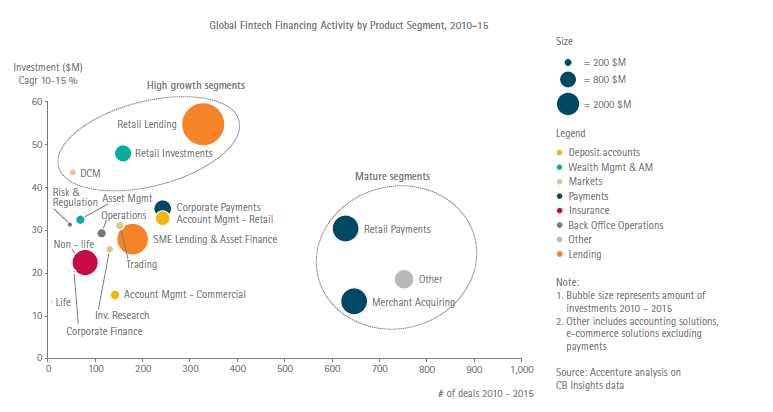 Another reason is that FinTech investors realize that the insurance industry is ripe for disruption. With annual premium revenue of around $5 trillion and assets under management heading toward $15 trillion, the global insurance industry is a huge market. It lags other sectors, notably the banking industry, in adopting digital technology. Insurers need to raise their spending on innovation to ward off rising competition and lure much-needed new customers.
See also: Secrets InsurTechs Need to Learn
The upswing in investment in InsurTech firms will have a major impact on the insurance industry around the world. Expect a host of new arrivals to appear in the insurance industry in the next 12 to 18 months. Some of these firms will be marketing niche solutions to established carriers and brokers. Others will be looking to grab a slice of the insurance market by offering specialized insurance products and services built around digital technology.
Bottom line…if you haven’t done so already, it’s time to decide how you will respond to InsurTech.
This article originally appeared at Accenture.
Another reason is that FinTech investors realize that the insurance industry is ripe for disruption. With annual premium revenue of around $5 trillion and assets under management heading toward $15 trillion, the global insurance industry is a huge market. It lags other sectors, notably the banking industry, in adopting digital technology. Insurers need to raise their spending on innovation to ward off rising competition and lure much-needed new customers.
See also: Secrets InsurTechs Need to Learn
The upswing in investment in InsurTech firms will have a major impact on the insurance industry around the world. Expect a host of new arrivals to appear in the insurance industry in the next 12 to 18 months. Some of these firms will be marketing niche solutions to established carriers and brokers. Others will be looking to grab a slice of the insurance market by offering specialized insurance products and services built around digital technology.
Bottom line…if you haven’t done so already, it’s time to decide how you will respond to InsurTech.
This article originally appeared at Accenture.
Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

John Cusano is Accenture’s senior managing director of global insurance. He is responsible for setting the industry group's overall vision, strategy, investment priorities and client relationships. Cusano joined Accenture in 1988 and has held a number of leadership roles in Accenture’s insurance industry practice.