Be on the Lookout for These 3 Tax Scams
There was a 400% increase in phishing and malware incidents during the 2016 tax season -- and the scammers are at it again.

There was a 400% increase in phishing and malware incidents during the 2016 tax season -- and the scammers are at it again.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Adam K. Levin is a consumer advocate and a nationally recognized expert on security, privacy, identity theft, fraud, and personal finance. A former director of the New Jersey Division of Consumer Affairs, Levin is chairman and founder of IDT911 (Identity Theft 911) and chairman and co-founder of Credit.com .
We foresee a convergence that will create an updated generation rather than the disruption (and perhaps destruction) that some predict.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Mark Breading is a partner at Strategy Meets Action, a Resource Pro company that helps insurers develop and validate their IT strategies and plans, better understand how their investments measure up in today's highly competitive environment and gain clarity on solution options and vendor selection.
In these disruptive times, small- to medium-sized insurers that want to remain relevant must -- and can -- heed the call of innovation.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Jim Leftwich has more than 30 years of leadership experience in risk management and insurance. In 2010, he founded CHSI Technologies, which offers SaaS enterprise management software for small insurance operations and government risk pools.
To sell an idea to stakeholders, buyers and users, we not only have to change what they think but how they think.

To sell an idea to stakeholders, buyers and users, we not only have to change what they think but how they think. Without the right mental model, they won’t see the problem, understand the benefits or choose to change. Mental models are like sorting hats; they are how our minds make sense of the world around us, the vast amount of information we process and intuitive perception of our actions and their consequences. They filter the signal from the noise.
For example, consider the mental model: "Life is like chess." If you believe this mental model, you’ll see life as a strategic game with winners and losers following set rules, and you may set the goal of winning. But if your mental model is that "life’s a beach," then you may see life as more fun, with no winners and losers and no rules. You may expect that forces beyond your control like the waves of the ocean can influence you but that you can use them to have fun.
See also: Innovation Happens at the Edge
Often dubbed as the “Monaco of the East,” Singapore the red dot has beaten a path to steady economic progress and prosperity since the 1970s. Much of the success can be attributed to the vision of one man, Lee Kuan Yew, Singapore’s first prime minister, who reigned for more than 30 years, making him the world’s longest serving prime minister. He was unafraid of challenging popular ideologies. Right up to the end of his life, Lee believed in constantly adapting to the changing realities of the world and refreshing his mental map. He sought the views of experts in industry, academia, politics and journalism. But having processed their arguments, he did not let himself be swayed if he absolutely believed something else was in the best long-term interest of Singapore. I was drawn to his vision and chose to move to Singapore to experience the economic miracle. I have seen first-hand how one man has changed how people think and as a result transformed Singapore from the "third world to the first world in a single generation."
See also: How to Master the ABCs of Innovation
Innovations that change the world need to be explained before they can be accepted. Brands that successfully sell their innovations have been able to change how we think, feel and connect with not only their products but ourselves and the world around us.
Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Shahzadi Jehangir is an innovation leader and expert in building trust and value in the digital age, creating scalable new businesses generating millions of dollars in revenue each year, with more than $10 million last year alone.
What does this mean for you? Fewer accidents, lower risks for workers, reduced workers' comp premiums.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Joseph Paduda, the principal of Health Strategy Associates, is a nationally recognized expert in medical management in group health and workers' compensation, with deep experience in pharmacy services. Paduda also leads CompPharma, a consortium of pharmacy benefit managers active in workers' compensation.
Artificial intelligence should never threaten workers’ comp if more pragmatic, technology-based strategies are implemented now.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Karen Wolfe is founder, president and CEO of MedMetrics. She has been working in software design, development, data management and analysis specifically for the workers' compensation industry for nearly 25 years. Wolfe's background in healthcare, combined with her business and technology acumen, has resulted in unique expertise.
Many people miss that, while insurance looks old and antiquated on the exterior, it is actually quite modern and vibrant on the interior.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Nick Lamparelli has been working in the insurance industry for nearly 20 years as an agent, broker and underwriter for firms including AIR Worldwide, Aon, Marsh and QBE. Simulation and modeling of natural catastrophes occupy most of his day-to-day thinking. Billions of dollars of properties exposed to catastrophe that were once uninsurable are now insured because of his novel approaches.
Risk managers need to start by embedding elements of analysis into decision-making processes, expanding the scope over time.

Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Alex Sidorenko has more than 13 years of strategic, innovation, risk and performance management experience across Australia, Russia, Poland and Kazakhstan. In 2014, he was named the risk manager of the year by the Russian Risk Management Association.
The AXA-Facebook strategic partnership was seen as a milestone in 2014, but what has actually happened?

Until now.
See also: How to Capture Data Using Social Media
In this overview, I will present three ways insurers can use social media to everyone’s advantage. 1) Outbound marketing
Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Erik Abrahamsson is the founder and CEO of Digital Fineprint, a London-based analytics company helping insurers use social media. In January 2017, it was picked as one of the top five insurtech companies worldwide for Accenture's Innovation Lab.
PwC's 20th CEO Survey finds that 86% see technology having major impact on competition within five years.

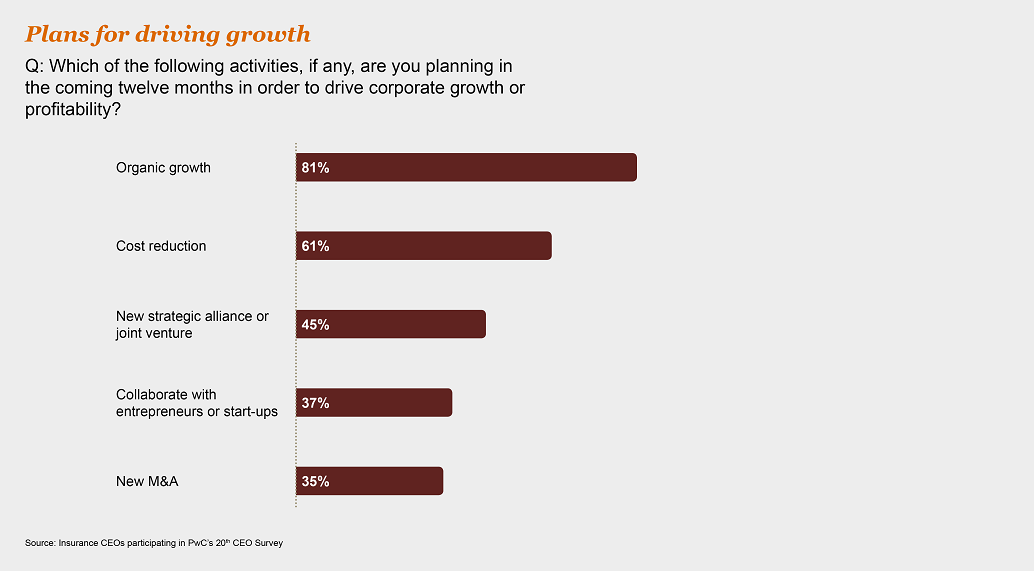
 Innovation and growth
86% of insurance CEOs believe technology will completely reshape competition in the industry or have a significant impact over the next five years. The gathering transformation is already evident in areas ranging from robo-advice to pay-as-you-go and sensor-based coverage.
See also: Convergence: Insurance in 2017
Cutting-edge customer interaction and data analytics have enabled insurtech businesses to set the pace in the marketplace. However, rather than being just a threat, collaboration with insurtech businesses can help more established insurers to make the leap from incremental to breakthrough innovation. This includes improving insurers’ ability to analyze the huge amounts of data at their disposal, which can lead to better customer understanding, higher win rates and more informed underwriting. Partnership with insurtech can help insurers improve processes, increase efficiencies and reduce costs.
Innovation and growth
86% of insurance CEOs believe technology will completely reshape competition in the industry or have a significant impact over the next five years. The gathering transformation is already evident in areas ranging from robo-advice to pay-as-you-go and sensor-based coverage.
See also: Convergence: Insurance in 2017
Cutting-edge customer interaction and data analytics have enabled insurtech businesses to set the pace in the marketplace. However, rather than being just a threat, collaboration with insurtech businesses can help more established insurers to make the leap from incremental to breakthrough innovation. This includes improving insurers’ ability to analyze the huge amounts of data at their disposal, which can lead to better customer understanding, higher win rates and more informed underwriting. Partnership with insurtech can help insurers improve processes, increase efficiencies and reduce costs.
 Data, digitization and trust
While digitization and data proliferation are now central elements of the insurance business, they bring increased cyber risk. More than eight out of 10 insurance CEOs (81%) are "somewhat" or "extremely" concerned about the impact on their growth prospects, on a par with banking and capital markets (82%).
Given the volume of medical, financial and other sensitive policyholder information that insurers hold, breaches could lead to a loss of trust that would be extremely difficult to restore. More than seven out of 10 insurance CEOs (72%) believe that it’s harder to sustain trust in this digitized world, though they also see the management of data as a competitive differentiator.
Data, digitization and trust
While digitization and data proliferation are now central elements of the insurance business, they bring increased cyber risk. More than eight out of 10 insurance CEOs (81%) are "somewhat" or "extremely" concerned about the impact on their growth prospects, on a par with banking and capital markets (82%).
Given the volume of medical, financial and other sensitive policyholder information that insurers hold, breaches could lead to a loss of trust that would be extremely difficult to restore. More than seven out of 10 insurance CEOs (72%) believe that it’s harder to sustain trust in this digitized world, though they also see the management of data as a competitive differentiator.
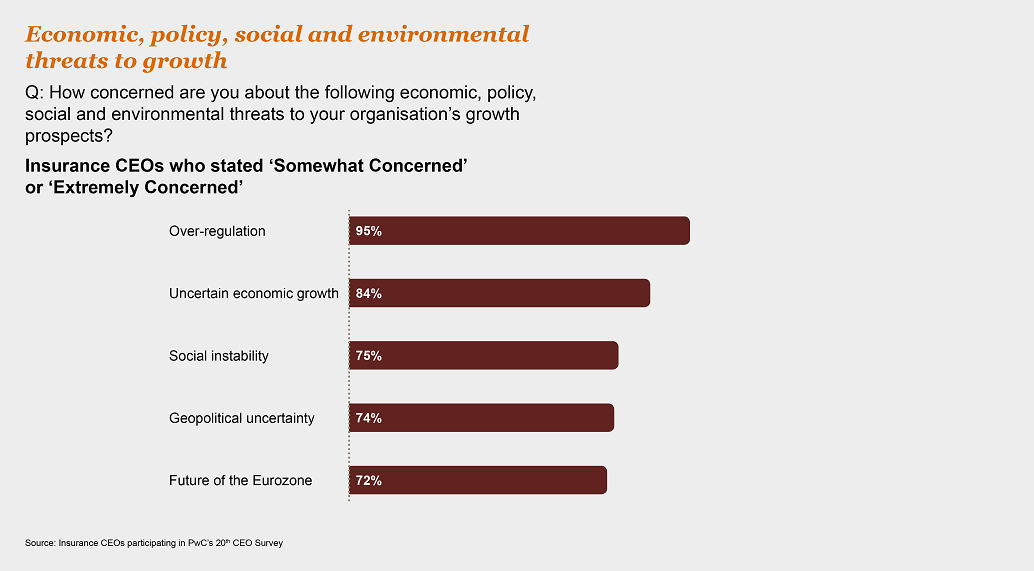
 Grappling with regulation
A massive 95% of insurance CEOs are at least "somewhat concerned" about the potential impact of over-regulation on their growth prospects, and 67% are "extremely concerned."
See also: Insurance Coverage Porn
The need to implement so many regulatory reforms across so many areas has inevitably tied up management’s time and made reporting more cumbersome. Compliance demands and costs also continue to rise, straining operational infrastructure and holding back returns. However, these are the unavoidable realities of today’s marketplace. Insurers that are able to build the changes into business as usual can gain a critical edge. And pressure on returns means the "second line" now has to pay its way as part of an approach that shifts the focus beyond compliance to sharpening competitive advantage.
Grappling with regulation
A massive 95% of insurance CEOs are at least "somewhat concerned" about the potential impact of over-regulation on their growth prospects, and 67% are "extremely concerned."
See also: Insurance Coverage Porn
The need to implement so many regulatory reforms across so many areas has inevitably tied up management’s time and made reporting more cumbersome. Compliance demands and costs also continue to rise, straining operational infrastructure and holding back returns. However, these are the unavoidable realities of today’s marketplace. Insurers that are able to build the changes into business as usual can gain a critical edge. And pressure on returns means the "second line" now has to pay its way as part of an approach that shifts the focus beyond compliance to sharpening competitive advantage.
 Download the full report here.
Download the full report here.
Get Involved
Our authors are what set Insurance Thought Leadership apart.
|
Partner with us
We’d love to talk to you about how we can improve your marketing ROI.
|

Jamie Yoder is president and general manager, North America, for Sapiens.
Previously, he was president of Snapsheet, Before Snapsheet, he led the insurance advisory practice at PwC.