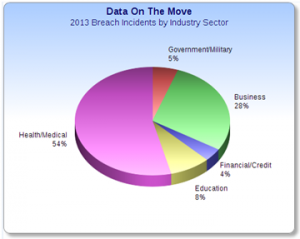
 For instance, in California, Palomar Health recently experienced a data breach when an encrypted laptop and two unencrypted flash drives were taken from a staff member's car. The devices exposed the personal health information of 5,000 patients. In Michigan in late January, a laptop computer and flash drive were stolen from an employee of the state Long Term Care (LTC) Ombudsman’s Office. Information on the laptop was encrypted, but data on the flash drive was not. The flash drive contained personal information about 2,595 living and deceased individuals, including names and addresses and, for some individuals, dates of birth. Either a Social Security number or a Medicaid identification number was included with 1,539 records.
Data breaches pose a significant risk to consumers because of the correlation between breaches and identity theft. According to Javelin Research, one out of three people whose information was breached fell victim to fraud in the same year. When medical records or personal health information (PHI) are compromised, consumers are not only facing an increased risk of medical identity theft. The risk for all types of identity theft is increased. (For more information on medical identity theft and its impact on the community, see the Medical Identity Theft and Fraud article on ITL).
The information entrusted to medical providers and insurance companies is often the same information that can be used to steal a person’s identity and commit financial identity theft, government identity theft and even criminal identity theft. In addition to receiving medical goods and services or prescriptions in the victim’s name, a thief could obtain loans or new lines of credit, apply for government benefits or file a false tax return. The perpetrator could even use the victim’s name if caught while committing a crime.
“Whether sensitive data is at rest or in transit, it should have appropriate risk-based controls and policies applied to its governance,” says Ann Patterson, program director with Medical Identity Fraud Association, which unites all the stakeholders and helps to convey the importance of these best practices. “The same judicious enterprise-wide data protection principles that you apply to your data at rest should also be considered for your data in transit and your mobile data. Particularly for mobile, BYOD policies (Bring Your Own Device) are essential.”
According to MIFA, many organizations are feeling the impact of shrinking budgets and may be tempted to reduce costs by limiting financial resources for internal fraud detection and prevention programs. This may provide immediate help to the bottom line. But in the long term it’s the wrong solution. Costs creep up in other areas when fraud is ignored. This could result in an organizational culture shift; as the old saying goes, what we allow, we encourage.
Coupled with human resources divisions, the fraud detection and prevention programs often provide employee training and formulate best practices in regard to fraud reduction.
The ITRC realizes the critical importance of information management and data security. We believe strongly in the importance of educating consumers and businesses about the value of our individual data and the importance of personally identifying information (PII). For this reason, our organization began tracking data breaches in 2005. Tracking breaches has allowed us to look for patterns in regard to how our information is being safeguarded, or compromised, by those we trust with it.
The ITRC defines a data breach as an event in which an individual name plus a Social Security number, driver’s license number, medical record or financial record (credit/debit cards included) is potentially put at risk because of exposure. This exposure can occur either electronically or in paper format. The ITRC will capture breaches that do not, by the nature of the incident, trigger data-breach-notification laws. Generally, these breaches consist of the exposure of user names, emails and passwords without involving sensitive personal identifying information. These breach incidents will be included by name but without the total number of records exposed. (For a more detailed explanation of our methods, visit the ITRC breach report page).
Data breaches and identity theft have been on the rise and have a significant effect on the individual victims as well as on the U.S. economy. We acknowledge that there is no panacea to rid ourselves of this issue entirely. However, encouraging negligence by not providing employees with the proper tools, and simply not acknowledging the problem, is not the answer, either.
Small and steady gains can be made by implementing training and increasing accountability for the individuals and organizations that we entrust to be good stewards of our PII. A good start would be to understand and recognize how each type of incident plays a role and identify deficiencies.
Another option for organizations is to get involved with industry and trade organizations that also tackle issues related to data breach best practices daily. Businesses want to keep proprietary information close to the vest, but best practices about breaches should not be a trade secret. A highly engaged and enlightened health/medical community would be a step in the right direction.
For instance, in California, Palomar Health recently experienced a data breach when an encrypted laptop and two unencrypted flash drives were taken from a staff member's car. The devices exposed the personal health information of 5,000 patients. In Michigan in late January, a laptop computer and flash drive were stolen from an employee of the state Long Term Care (LTC) Ombudsman’s Office. Information on the laptop was encrypted, but data on the flash drive was not. The flash drive contained personal information about 2,595 living and deceased individuals, including names and addresses and, for some individuals, dates of birth. Either a Social Security number or a Medicaid identification number was included with 1,539 records.
Data breaches pose a significant risk to consumers because of the correlation between breaches and identity theft. According to Javelin Research, one out of three people whose information was breached fell victim to fraud in the same year. When medical records or personal health information (PHI) are compromised, consumers are not only facing an increased risk of medical identity theft. The risk for all types of identity theft is increased. (For more information on medical identity theft and its impact on the community, see the Medical Identity Theft and Fraud article on ITL).
The information entrusted to medical providers and insurance companies is often the same information that can be used to steal a person’s identity and commit financial identity theft, government identity theft and even criminal identity theft. In addition to receiving medical goods and services or prescriptions in the victim’s name, a thief could obtain loans or new lines of credit, apply for government benefits or file a false tax return. The perpetrator could even use the victim’s name if caught while committing a crime.
“Whether sensitive data is at rest or in transit, it should have appropriate risk-based controls and policies applied to its governance,” says Ann Patterson, program director with Medical Identity Fraud Association, which unites all the stakeholders and helps to convey the importance of these best practices. “The same judicious enterprise-wide data protection principles that you apply to your data at rest should also be considered for your data in transit and your mobile data. Particularly for mobile, BYOD policies (Bring Your Own Device) are essential.”
According to MIFA, many organizations are feeling the impact of shrinking budgets and may be tempted to reduce costs by limiting financial resources for internal fraud detection and prevention programs. This may provide immediate help to the bottom line. But in the long term it’s the wrong solution. Costs creep up in other areas when fraud is ignored. This could result in an organizational culture shift; as the old saying goes, what we allow, we encourage.
Coupled with human resources divisions, the fraud detection and prevention programs often provide employee training and formulate best practices in regard to fraud reduction.
The ITRC realizes the critical importance of information management and data security. We believe strongly in the importance of educating consumers and businesses about the value of our individual data and the importance of personally identifying information (PII). For this reason, our organization began tracking data breaches in 2005. Tracking breaches has allowed us to look for patterns in regard to how our information is being safeguarded, or compromised, by those we trust with it.
The ITRC defines a data breach as an event in which an individual name plus a Social Security number, driver’s license number, medical record or financial record (credit/debit cards included) is potentially put at risk because of exposure. This exposure can occur either electronically or in paper format. The ITRC will capture breaches that do not, by the nature of the incident, trigger data-breach-notification laws. Generally, these breaches consist of the exposure of user names, emails and passwords without involving sensitive personal identifying information. These breach incidents will be included by name but without the total number of records exposed. (For a more detailed explanation of our methods, visit the ITRC breach report page).
Data breaches and identity theft have been on the rise and have a significant effect on the individual victims as well as on the U.S. economy. We acknowledge that there is no panacea to rid ourselves of this issue entirely. However, encouraging negligence by not providing employees with the proper tools, and simply not acknowledging the problem, is not the answer, either.
Small and steady gains can be made by implementing training and increasing accountability for the individuals and organizations that we entrust to be good stewards of our PII. A good start would be to understand and recognize how each type of incident plays a role and identify deficiencies.
Another option for organizations is to get involved with industry and trade organizations that also tackle issues related to data breach best practices daily. Businesses want to keep proprietary information close to the vest, but best practices about breaches should not be a trade secret. A highly engaged and enlightened health/medical community would be a step in the right direction.
'Data on the Move' Means Data at Risk
Breaches related to "data on the move" in healthcare are rising, but there are simple ways to address the problem.

 For instance, in California, Palomar Health recently experienced a data breach when an encrypted laptop and two unencrypted flash drives were taken from a staff member's car. The devices exposed the personal health information of 5,000 patients. In Michigan in late January, a laptop computer and flash drive were stolen from an employee of the state Long Term Care (LTC) Ombudsman’s Office. Information on the laptop was encrypted, but data on the flash drive was not. The flash drive contained personal information about 2,595 living and deceased individuals, including names and addresses and, for some individuals, dates of birth. Either a Social Security number or a Medicaid identification number was included with 1,539 records.
Data breaches pose a significant risk to consumers because of the correlation between breaches and identity theft. According to Javelin Research, one out of three people whose information was breached fell victim to fraud in the same year. When medical records or personal health information (PHI) are compromised, consumers are not only facing an increased risk of medical identity theft. The risk for all types of identity theft is increased. (For more information on medical identity theft and its impact on the community, see the Medical Identity Theft and Fraud article on ITL).
The information entrusted to medical providers and insurance companies is often the same information that can be used to steal a person’s identity and commit financial identity theft, government identity theft and even criminal identity theft. In addition to receiving medical goods and services or prescriptions in the victim’s name, a thief could obtain loans or new lines of credit, apply for government benefits or file a false tax return. The perpetrator could even use the victim’s name if caught while committing a crime.
“Whether sensitive data is at rest or in transit, it should have appropriate risk-based controls and policies applied to its governance,” says Ann Patterson, program director with Medical Identity Fraud Association, which unites all the stakeholders and helps to convey the importance of these best practices. “The same judicious enterprise-wide data protection principles that you apply to your data at rest should also be considered for your data in transit and your mobile data. Particularly for mobile, BYOD policies (Bring Your Own Device) are essential.”
According to MIFA, many organizations are feeling the impact of shrinking budgets and may be tempted to reduce costs by limiting financial resources for internal fraud detection and prevention programs. This may provide immediate help to the bottom line. But in the long term it’s the wrong solution. Costs creep up in other areas when fraud is ignored. This could result in an organizational culture shift; as the old saying goes, what we allow, we encourage.
Coupled with human resources divisions, the fraud detection and prevention programs often provide employee training and formulate best practices in regard to fraud reduction.
The ITRC realizes the critical importance of information management and data security. We believe strongly in the importance of educating consumers and businesses about the value of our individual data and the importance of personally identifying information (PII). For this reason, our organization began tracking data breaches in 2005. Tracking breaches has allowed us to look for patterns in regard to how our information is being safeguarded, or compromised, by those we trust with it.
The ITRC defines a data breach as an event in which an individual name plus a Social Security number, driver’s license number, medical record or financial record (credit/debit cards included) is potentially put at risk because of exposure. This exposure can occur either electronically or in paper format. The ITRC will capture breaches that do not, by the nature of the incident, trigger data-breach-notification laws. Generally, these breaches consist of the exposure of user names, emails and passwords without involving sensitive personal identifying information. These breach incidents will be included by name but without the total number of records exposed. (For a more detailed explanation of our methods, visit the ITRC breach report page).
Data breaches and identity theft have been on the rise and have a significant effect on the individual victims as well as on the U.S. economy. We acknowledge that there is no panacea to rid ourselves of this issue entirely. However, encouraging negligence by not providing employees with the proper tools, and simply not acknowledging the problem, is not the answer, either.
Small and steady gains can be made by implementing training and increasing accountability for the individuals and organizations that we entrust to be good stewards of our PII. A good start would be to understand and recognize how each type of incident plays a role and identify deficiencies.
Another option for organizations is to get involved with industry and trade organizations that also tackle issues related to data breach best practices daily. Businesses want to keep proprietary information close to the vest, but best practices about breaches should not be a trade secret. A highly engaged and enlightened health/medical community would be a step in the right direction.
For instance, in California, Palomar Health recently experienced a data breach when an encrypted laptop and two unencrypted flash drives were taken from a staff member's car. The devices exposed the personal health information of 5,000 patients. In Michigan in late January, a laptop computer and flash drive were stolen from an employee of the state Long Term Care (LTC) Ombudsman’s Office. Information on the laptop was encrypted, but data on the flash drive was not. The flash drive contained personal information about 2,595 living and deceased individuals, including names and addresses and, for some individuals, dates of birth. Either a Social Security number or a Medicaid identification number was included with 1,539 records.
Data breaches pose a significant risk to consumers because of the correlation between breaches and identity theft. According to Javelin Research, one out of three people whose information was breached fell victim to fraud in the same year. When medical records or personal health information (PHI) are compromised, consumers are not only facing an increased risk of medical identity theft. The risk for all types of identity theft is increased. (For more information on medical identity theft and its impact on the community, see the Medical Identity Theft and Fraud article on ITL).
The information entrusted to medical providers and insurance companies is often the same information that can be used to steal a person’s identity and commit financial identity theft, government identity theft and even criminal identity theft. In addition to receiving medical goods and services or prescriptions in the victim’s name, a thief could obtain loans or new lines of credit, apply for government benefits or file a false tax return. The perpetrator could even use the victim’s name if caught while committing a crime.
“Whether sensitive data is at rest or in transit, it should have appropriate risk-based controls and policies applied to its governance,” says Ann Patterson, program director with Medical Identity Fraud Association, which unites all the stakeholders and helps to convey the importance of these best practices. “The same judicious enterprise-wide data protection principles that you apply to your data at rest should also be considered for your data in transit and your mobile data. Particularly for mobile, BYOD policies (Bring Your Own Device) are essential.”
According to MIFA, many organizations are feeling the impact of shrinking budgets and may be tempted to reduce costs by limiting financial resources for internal fraud detection and prevention programs. This may provide immediate help to the bottom line. But in the long term it’s the wrong solution. Costs creep up in other areas when fraud is ignored. This could result in an organizational culture shift; as the old saying goes, what we allow, we encourage.
Coupled with human resources divisions, the fraud detection and prevention programs often provide employee training and formulate best practices in regard to fraud reduction.
The ITRC realizes the critical importance of information management and data security. We believe strongly in the importance of educating consumers and businesses about the value of our individual data and the importance of personally identifying information (PII). For this reason, our organization began tracking data breaches in 2005. Tracking breaches has allowed us to look for patterns in regard to how our information is being safeguarded, or compromised, by those we trust with it.
The ITRC defines a data breach as an event in which an individual name plus a Social Security number, driver’s license number, medical record or financial record (credit/debit cards included) is potentially put at risk because of exposure. This exposure can occur either electronically or in paper format. The ITRC will capture breaches that do not, by the nature of the incident, trigger data-breach-notification laws. Generally, these breaches consist of the exposure of user names, emails and passwords without involving sensitive personal identifying information. These breach incidents will be included by name but without the total number of records exposed. (For a more detailed explanation of our methods, visit the ITRC breach report page).
Data breaches and identity theft have been on the rise and have a significant effect on the individual victims as well as on the U.S. economy. We acknowledge that there is no panacea to rid ourselves of this issue entirely. However, encouraging negligence by not providing employees with the proper tools, and simply not acknowledging the problem, is not the answer, either.
Small and steady gains can be made by implementing training and increasing accountability for the individuals and organizations that we entrust to be good stewards of our PII. A good start would be to understand and recognize how each type of incident plays a role and identify deficiencies.
Another option for organizations is to get involved with industry and trade organizations that also tackle issues related to data breach best practices daily. Businesses want to keep proprietary information close to the vest, but best practices about breaches should not be a trade secret. A highly engaged and enlightened health/medical community would be a step in the right direction.






